Quiz Summary
0 of 48 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Results
0 of 48 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the practice exam, but hey, you have unlimited access.😎
Practise makes you perfect! 👊 -
Congratulations! 🥳
You have passed the practice exam successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path.✌️
Good luck with the exam! Stay strong.👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 48
1. Question
What can be accomplished with a brute-force attack?
CorrectIncorrect -
Question 2 of 48
2. Question
A ____________ is malicious software that is hidden and packaged inside other software that looks normal and legitimate.
CorrectIncorrect -
Question 3 of 48
3. Question
Which of the following protocols are examples of TCP/IP data-link layer protocols? (Choose two answers.)
CorrectIncorrect -
Question 4 of 48
4. Question
The __________ is used specifically to identify the entity created when encapsulating data inside data-link layer headers and trailers.
CorrectIncorrect -
Question 5 of 48
5. Question
The senior network engineer assigned you the following task:
-
Create a VLAN with vlan-id 4
-
Name the VLAN as examsdigest-vlan
-
Assign the ports Fa0/10 – Fa0/14 to that VLAN
-
Make the ports always to operate in access mode
-
examsdigest#
Enter configuration commands, one per line. End with CNTL/Z.
examsdigest(config)#
examsdigest(config-vlan)#
examsdigest(config-vlan)# exit
examsdigest(config)#
examsdigest(config-if)#
examsdigest(config-if)#
examsdigest(config-if)# end
CorrectIncorrect -
-
Question 6 of 48
6. Question
The following diagram illustrates a LAN design with data in VLAN 6 and phones in VLAN 5. Using the diagram below configure the Switch using ports F0/3 – F0/5 to match the LAN design.
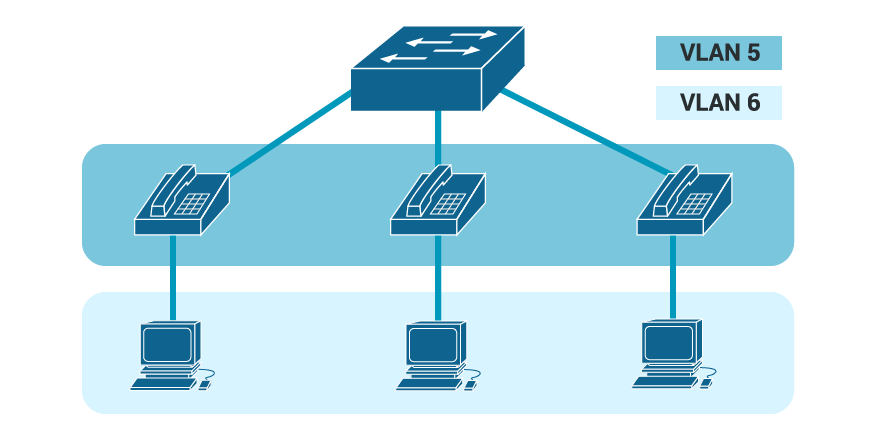
-
examsdigest#
Enter configuration commands, one per line. End with CNTL/Z.
examsdigest(config)#
examsdigest(config-vlan)#
examsdigest(config-vlan)#
examsdigest(config-if)#
examsdigest(config-if)#
examsdigest(config-if)#
examsdigest(config-if)#^Z
examsdigest#
CorrectIncorrect -
-
Question 7 of 48
7. Question
When APs are placed at different geographic locations, they can all be interconnected by a switched infrastructure. The 802.11 standard calls this an extended service set (ESS).
CorrectIncorrect -
Question 8 of 48
8. Question
Which of the following IEEE 802.11 Wi-Fi standards use the 2.4 GHz band? (Choose all that apply)
CorrectIncorrect -
Question 9 of 48
9. Question
Your task is to troubleshoot a user’s PC with IP 10.20.30.5 and mask 255.255.255.0. Based on the given details type the number of the network (N), subnet (S), and host (H) bits.
-
Network bits (N) =
Subnet bits (S) =
Host bits (H) =
CorrectIncorrect -
-
Question 10 of 48
10. Question
Your task is to troubleshoot a user’s PC with IP 192.168.100.1/28. Based on the given details type the number of the network (N), subnet (S), and host (H) bits.
-
Network bits (N) =
Subnet bits (S) =
Host bits (H) =
CorrectIncorrect -
-
Question 11 of 48
11. Question
Which of the following masks, when used within a Class B network, would supply enough subnet bits to support 90 subnets? (Choose two)
CorrectIncorrect -
Question 12 of 48
12. Question
Type the required commands by following the steps below:
-
!Step 1: Move from enable mode to global configuration mode
Switch#!Step 2: Change the switch’s name to Examsdigest
Switch(config)#!Step 3: Move from global configuration mode to console line configuration mode
Examsdigest(config)#!Step 4: Set the console’s simple password to examsdigest
Examsdigest(config-line)#!Step 5: Move from console configuration mode to FastEthernet 0/3 interface configuration mode
Examsdigest(config-line)#!Step 6: Set the speed to 100 Mbps for interface FastEthernet 0/3
Examsdigest(config-if)#Examsdigest(config-if)# exit
Examsdigest(config)#
CorrectIncorrect -
-
Question 13 of 48
13. Question
Match the four main types of memory found in Cisco switches with the most common use of each type.
Sort elements
- RAM
- Flash memory
- ROM
- NVRAM
-
Is used by the switch for working storage. The running (active) configuration file is stored here.
-
Stores fully functional Cisco IOS images and is the default location where the switch gets its Cisco IOS at boot time. Also can be used to store any other files, including backup copies of configuration files.
-
Stores a bootstrap program that is loaded when the switch first powers on. This bootstrap program then finds the full Cisco IOS image and manages the process of loading Cisco IOS into RAM, at which point Cisco IOS takes over the operation of the switch.
-
Stores the initial or startup configuration file that is used when the switch is first powered on and when the switch is reloaded.
CorrectIncorrect -
Question 14 of 48
14. Question
Type the access-list command that permits all packets sent from hosts in subnet 14.15.16.0/24. Use the ACL number 50 for the ACL rule.
CorrectIncorrect -
-
Question 15 of 48
15. Question
The senior network engineer assigns you a task that requires ACL configuration. He provides the following diagram and the requirements below:
1) Enable the ACL inbound on R2’s G0/1 interface.
2) Permit packets coming from the host with IP 20.2.2.1
3) Deny packets coming from the rest subnet 20.2.2.0/24
4) Permit packets coming from a network with subnet 155.165.0.0/16Now you are responsible to configure the R2 using the ACL standard number 1.
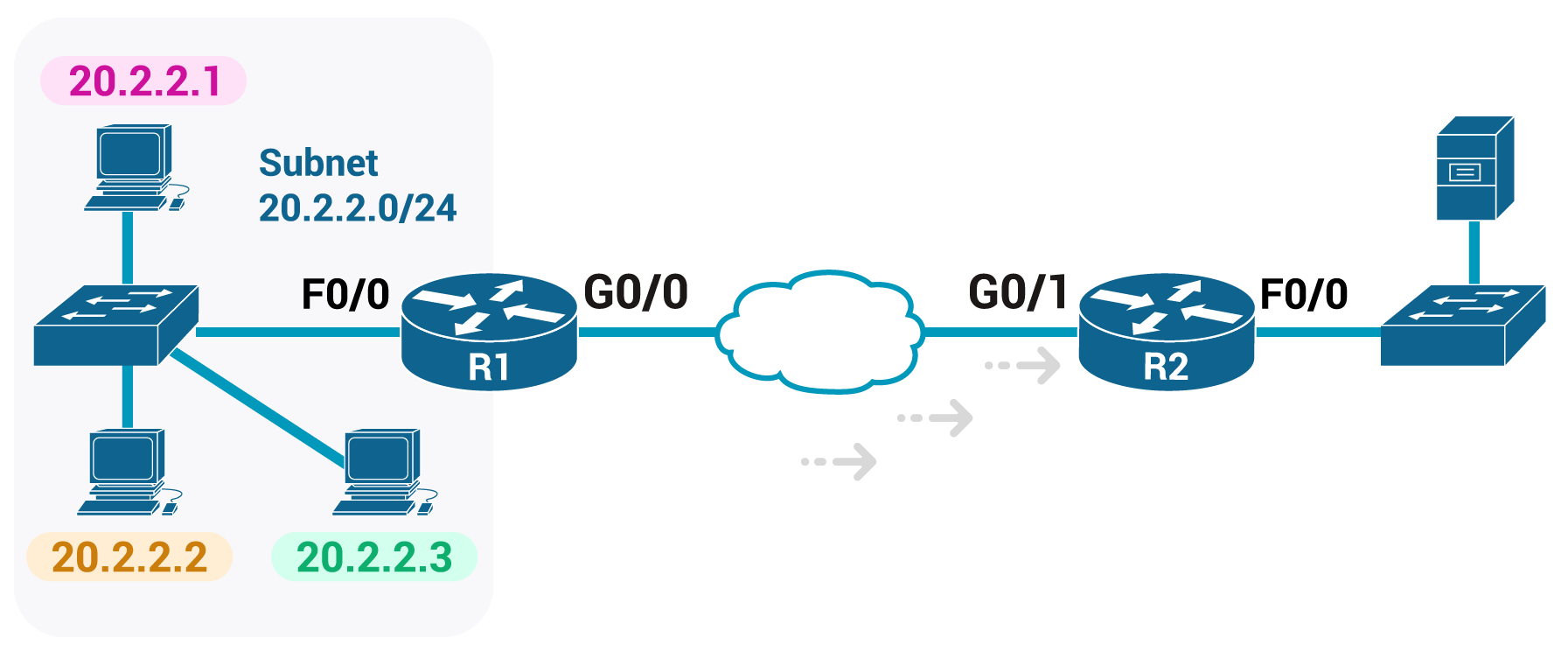
-
R2#
Enter configuration commands, one per line. End with CNTL/Z.! Permit packets coming from the host with IP 20.2.2.1
R2(config)#! Deny packets coming from the rest subnet 20.2.2.0/24
R2(config)#! Permit packets coming from a network with subnet 155.165.0.0/16
R2(config)#! Enable the ACL inbound on R2’s G0/1 interface.
R2(config)#
R2(config-if)#
R2(config-if)# ^Z
R2#
CorrectIncorrect -
-
Question 16 of 48
16. Question
Your task is to type a one-line standard ACL that matches the following criteria. All access-list commands use the number 1 in the command.
-
Criteria #1: Permit packets from 186.33.2.3
ACL command #1:
Criteria #2: Permit packets from hosts with 56.57.2 as the first three octets
ACL command #2:
Criteria #3: Permit packets from hosts with 56.57 as the first two octets
ACL command #3:
Criteria #4: Permit packets from any host
ACL command #4:
CorrectIncorrect -
-
Question 17 of 48
17. Question
Given the following configuration command outputs. Match the Network Address Translation methods (PAT or Dynamic NAT) with the respective configuration commands.
Sort elements
- PAT
- DNAT
-
ExamsDigestR1# show running-config
interface GigabitEthernet0/0
ip address 192.168.1.3 255.255.255.0
ip nat inside
interface Serial0/0/0
ip address 100.1.1.249 255.255.255.252 ip nat outside
ip nat inside source list 1 interface Serial0/0/0 overload
access-list 1 permit 192.168.1.2
access-list 1 permit 192.168.1.1
-
ExamsDigestR2# show running-config
interface GigabitEthernet0/0
ip address 192.168.1.3 255.255.255.0
ip nat inside
interface Serial0/0/0
ip address 100.1.1.251 255.255.255.0
ip nat outside
ip nat pool examsdigest 100.1.1.1 100.1.1.2 netmask 255.255.255.252
ip nat inside source list 1 pool examsdigest
access-list 1 permit 192.168.1.2
access-list 1 permit 192.168.1.1
CorrectIncorrect -
Question 18 of 48
18. Question
Which of the following characteristics of network traffic can be managed by Quality of Service (QoS)? (Choose all that apply)
CorrectIncorrect -
Question 19 of 48
19. Question
Match the Cisco QoS toolsets with the respective description.
Sort elements
- Classification and Marking
- Queuing
- Shaping and Policing
- Congestion Avoidance
-
QoS categorize packets by examining the contents of the frame, and packet headers, and change the packet headers
-
QoS allows you to control congestion by determining the order in which packets are sent out an interface based on priorities assigned to those packets
-
QoS monitors the bit rate of the messages that flow through a device.
-
QoS attempts to reduce overall packet loss by preemptively discarding some packets used in TCP connections.
CorrectIncorrect -
Question 20 of 48
20. Question
End-user hosts need to know the IPv6 address of a default router, to which the host sends IPv6 packets if the host is in a different subnet.
CorrectIncorrect -
Question 21 of 48
21. Question
Answer the following fill-in the blank by typing the abbreviated form of the IPv6 address and vice versa.
-
Full IPv6: 2340:0000:0010:0100:1000:ABCD:0101:1010
Abbreviated form: : : : : : : :
Full IPv6: : : : : : : :
Abbreviated form: 30A0:ABCD:EF12:3456:ABC:B8B8:1234:5002
Full IPv6: : : : : : : :
Abbreviated form: 1230::
CorrectIncorrect -
-
Question 22 of 48
22. Question
Which of the following addresses are not valid Class A network IDs? (Choose all that apply)
CorrectIncorrect -
Question 23 of 48
23. Question
What information can you extract having the IP address 172.16.99.45? (Choose two answers.)
CorrectIncorrect -
Question 24 of 48
24. Question
A router lists the following partial output from the
show ip routecommand. Out which interface will the router route packets destined to IP address 180.5.38.122?
10.0.0.0/8 is variably subnetted, 8 subnets, 5 masks
O 180.5.38.100/32 [110/50] via 172.16.25.2, 00:00:04, GigabitEthernet0/0/0
O 180.5.38.64/26 [110/100] via 172.16.25.129, 00:00:09, GigabitEthernet0/1/0
O 180.5.37.0/23 [110/65] via 172.16.24.2, 00:00:04, GigabitEthernet0/2/0
O 180.5.38.96/27 [110/65] via 172.16.24.129, 00:00:09, GigabitEthernet0/3/0
O 0.0.0.0/0 [110/129] via 172.16.25.129, 00:00:09, GigabitEthernet0/0/0CorrectIncorrect -
Question 25 of 48
25. Question
Type the commands that produce the following outputs.
-
List the router’s entire routing table:
List the details of static routes only:
List detailed information about the route 156.10.2.0:
CorrectIncorrect -
-
Question 26 of 48
26. Question
How many object keys can be found in the JSON object sample below?
{
“response”: {
“id”: “3”,
“name”: “Cisco Catalyst”,
“ipAddress”: {
“private”: “192.168.1.1”,
“public” : “156.157.1.1”
}
}
}CorrectIncorrect -
Question 27 of 48
27. Question
CRUD is the acronym of the four primary actions performed by an application. What does CRUD stand for? (Type only the remaining words)
-
C
R
U
D
CorrectIncorrect -
-
Question 28 of 48
28. Question
Identify the hostname part from the given URI:
https://cluster.cisco.com/dna/intent/api/v1/business/sda/fabric?ipaddress=10.1.2.3
CorrectIncorrect -
Question 29 of 48
29. Question
The process of dividing a physical server into multiple unique and isolated virtual servers by means of a software application is called server ______________.
CorrectIncorrect -
Question 30 of 48
30. Question
One of the differences between Public Cloud and Private Cloud (On-Premise) is that on the Public Cloud solution you are responsible for all management, maintenance, and updating of data centers.
CorrectIncorrect -
Question 31 of 48
31. Question
Which of the following network command following the command
router ospf 1, tells the router to start using OSPF on interfaces whose IP addresses are 20.1.20.1, 20.1.30.1, and 20.1.40.1?CorrectIncorrect -
Question 32 of 48
32. Question
Type the command that lists the OSPF neighbors off interface serial 0/1?
CorrectIncorrect -
-
Question 33 of 48
33. Question
Type the command that produces the following output.
-
R1#
Codes: L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2! Additional lines omitted for brevity
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 9 subnets, 2 masks
O 10.1.1.0/24 [110/2] via 10.1.14.1, 00:19:24, GigabitEthernet0/0/0
O 10.1.2.0/24 [110/2] via 10.1.14.1, 00:19:24, GigabitEthernet0/0/0
C 10.1.4.0/24 is directly connected, Vlan3
L 10.1.4.4/32 is directly connected, Vlan3
O 10.1.12.0/24 [110/2] via 10.1.14.1, 00:17:24, GigabitEthernet0/0/0
O 10.1.13.0/24 [110/2] via 10.1.14.1, 00:14:15, GigabitEthernet0/0/0
C 10.1.14.0/24 is directly connected, GigabitEthernet0/0/0
L 10.1.14.4/32 is directly connected, GigabitEthernet0/0/0
O 10.1.23.0/24 [110/3] via 10.1.14.1, 00:15:35, GigabitEthernet0/0/0
CorrectIncorrect -
-
Question 34 of 48
34. Question
Match the type of human security vulnerabilities attacks with the respective intentions.
Sort elements
- Social engineering
- Phishing
- Whaling
- Pharming
-
Exploits human trust and social behavior
-
Is the attempt to obtain sensitive information such as passwords and credit card details by disguising oneself as a trustworthy entity
-
Is a type of attack that targets high-profile employees, such as the CEO or CFO, in order to steal sensitive information from a company
-
Uses legitimate services to send users to a compromised site
CorrectIncorrect -
Question 35 of 48
35. Question
Answer the fill-in-the-blank by typing the correct protocol:
-
AAA servers usually support the protocol TACACS+ and to communicate with enterprise resources.
CorrectIncorrect -
-
Question 36 of 48
36. Question
A next-generation firewall sits at the edge of a company’s connection to the Internet. A network engineer has been configured to prevent Telnet clients residing on the Internet from accessing Telnet servers inside the company. Which of the following might a next-generation firewall use that a traditional firewall would not?
CorrectIncorrect -
Question 37 of 48
37. Question
If the devices below were connected with UTP Ethernet cables, which pairs of devices would require a straight-through cable? (Choose two answers.)
CorrectIncorrect -
Question 38 of 48
38. Question
Sort the following steps (from step 1 to step 4) in order to troubleshoot VLANs and VLAN Trunks
-
Confirm that all VLANs are both defined and active.
-
Check for incorrect trunk configuration settings that result in one switch operating as a trunk, with the neighboring switch not operating as a trunk.
-
Check the native VLAN settings on both ends of the trunk to ensure the settings match.
-
Check the allowed VLAN lists on both ends of each trunk to ensure that all VLANs intended to be used are included.
View Answers:
CorrectIncorrect -
-
Question 39 of 48
39. Question
Which of the following IEEE 802.11 Wi-Fi standards use the 5 GHz band? (Choose all that apply)
CorrectIncorrect -
Question 40 of 48
40. Question
A lightweight access point in which one of the following architectures participate?
CorrectIncorrect -
Question 41 of 48
41. Question
Which of the following IPv6 addresses appears to be a unique local unicast address? (Choose two)
CorrectIncorrect -
Question 42 of 48
42. Question
Match the access-list statements with their logic.
Sort elements
- access-list 101 deny udp any gt 10455 host 30.3.3.3 eq 25
- access-list 101 deny udp any lt 10455 host 30.3.3.3 eq 25
- access-list 101 deny udp host 30.3.3.3 gt 10455 any eq 25
- access-list 101 deny udp host 30.3.3.3 lt 10455 any eq 25
-
Deny packets with a UDP header, any source IP address with source port greater than 10455, a destination IP address 30.3.3.3 and a destination port equal to 25.
-
Deny packets with a UDP header, any source IP address with source port less than 10455, a destination IP address 30.3.3.3 and a destination port equal to 25.
-
Deny packets with a UDP header, a source IP address 30.3.3.3 and a source port greater than 10455, any destination IP address 30.3.3.3 with destination port equal to 25.
-
Deny packets with a UDP header, a source IP address 30.3.3.3 and a source port less than 10455, any destination IP address 30.3.3.3 with destination port equal to 25.
CorrectIncorrect -
Question 43 of 48
43. Question
R1 and R2 are attached to the same Ethernet VLAN, with subnet 192.168.1.0/24, and addresses 192.168.1.1, 192.168.2 respectively. The routers use an FHRP. Host A and host B attach to the same LAN and have correct default router settings per the FHRP configuration. Which of the following statements is true for this LAN?
CorrectIncorrect -
Question 44 of 48
44. Question
One of the features of SNMPv3 is called message integrity.
CorrectIncorrect -
Question 45 of 48
45. Question
Subnet masks can be written as 32-bit binary numbers, but not just any binary number. In particular, the binary subnet mask must follow these rules:
-
The value must not interleave 1s and 0s.
-
If 0s exist, they are on the left.
-
If 1s exist, they are on the right.
CorrectIncorrect -
-
Question 46 of 48
46. Question
Convert the following binary masks to decimal masks.
-
Binary mask: 11111111.11111111.11000000.00000000
Decimal mask: . . .
Binary mask: 11111111.11100000.00000000.00000000
Decimal mask: . . .
Binary mask: 11111110.00000000.00000000.00000000
Decimal mask: . . .
Binary mask: 11111111.11111100.00000000.00000000
Decimal mask: . . .
CorrectIncorrect -
-
Question 47 of 48
47. Question
Type the command that lists the contents of the startup-config (initial config) file.
CorrectIncorrect -
-
Question 48 of 48
48. Question
Which of the following statements describes part of the process of how a switch decides to forward a frame destined for a known unicast MAC address?
CorrectIncorrect