Time limit: 0
Quiz Summary
0 of 50 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Quiz complete. Results are being recorded.
Results
0 of 50 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the practice exam, but hey, you have unlimited access.😎
Practice makes you perfect! 👊 -
Congratulations! 🥳
You have passed the practice exam successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path. ✌️
Good luck with the exam! Stay strong. 👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 50
1. Question
Your laptop is running Windows 10 and starts getting slower and slower over time. After a quick investigation, you notice that the CPU utilization is between 85% and 95%. Then you start closing open applications to drop the CPU utilization. Unfortunately, the next day the issue with the CPU utilization happens again. Which of the following tools can you use to check the CPU utilization on Windows 10?
CorrectIncorrect -
Question 2 of 50
2. Question
You are troubleshooting an issue using your laptop which is running Windows 10. You need to display all the active TCP connections on the workstation. You open the command prompt. Which of the following commands should you use?
CorrectIncorrect -
Question 3 of 50
3. Question
You just bought the brand new MacBook Pro, 2.3GHz 8-Core Processor, 1TB Storage, and AMD Radeon Pro 5500M. You then decide to install Windows 10 on it because of the software you often use; they run on Windows environment but not compatible with the macOS. To allow both operating systems to exist on your brand new MacBook Pro, which of the following tools should you use?
CorrectIncorrect -
Question 4 of 50
4. Question
You are working with the products of VMware using your Mac OS. You are trying to install an Ubuntu 20.04 Focal Fossa on a virtual machine but after numerous attempts, you keep getting error messages. You review your VM’s specification and notice that you have configured the VM with 10GB of hard drive space, 2 GHz dual-core processor and 4 GiB RAM (system memory). Which of the following actions should you perform to install Ubuntu on the virtual machine (VM)?
CorrectIncorrect -
Question 5 of 50
5. Question
Which of the following MacOS built-in utilities should be used to restore access to the files that have been deleted?
CorrectIncorrect -
Question 6 of 50
6. Question
You have been tasked to install Windows 10 on one of your co-worker’s workstations. What is the minimum amount of hard drive space needed to install Windows 10 on a 64-bit system?
CorrectIncorrect -
Question 7 of 50
7. Question
Your Windows 10 workstation crashes from time to time. At first, you didn’t pay attention to this but as time goes on, you are unable to find out what’s the cause of these crashes. Which of the following tools should you use next to identify the cause of the system crash?
CorrectIncorrect -
Question 8 of 50
8. Question
Your manager announces that 2 workstations were stolen from the company. The workstations include important files and financial statements that were unencrypted. Your manager needs your help to provide a solution to keep files encrypted and secure on all devices running Windows in case of loss. Which of the following tools should you use to meet the requirement?
CorrectIncorrect -
Question 9 of 50
9. Question
You are trying to locate some .dll and .ocx files to edit and send them to your co-worker, but you are unable to see the files. Which of the following Control Panel utility should you use to find the hidden files?
CorrectIncorrect -
Question 10 of 50
10. Question
Which of the following file systems is used for organizing files on a Macintosh hard disk?
CorrectIncorrect -
Question 11 of 50
11. Question
You are using a Master Boot Record disk for dividing your disk into multiple partitions, each a maximum of 2.2TB. Which of the following type of partitions have a limit of one partition?
CorrectIncorrect -
Question 12 of 50
12. Question
After you’ve successfully installed a new hard drive in a Windows 10 system you have been tasked to create partitions on it. Which of the following tools should you use to create the partitions on the new hard drive?
CorrectIncorrect -
Question 13 of 50
13. Question
The senior network engineer of your company just notifies you that one of the web servers is down and the hosted-websites on this server return 503 status error code. You open your workstation to confirm the issue, which of the following commands will you type first to test if the webserver is reachable or not?
CorrectIncorrect -
Question 14 of 50
14. Question
You have been tasked to take incremental backups from the Windows server every morning at 5:00 AM. You need a tool that will automatically notify your manager of the backup completion. Which of the following tools should you use to meet the requirement?
CorrectIncorrect -
Question 15 of 50
15. Question
Assuming you are working in a Linux environment, trying to troubleshoot a network connectivity issue. You need to find out the IP address and the subnet mask of the current workstation, using the command prompt. Which of the following commands would be used to display the IP address and subnet mask of the workstation?
CorrectIncorrect -
Question 16 of 50
16. Question
You have recently been hired as an IT security specialist by a small company to improve the security of their wireless network. You have been tasked to harden the wireless network infrastructure to the highest possible level. Which of the following protocol encryption methods should you implement for the BEST security? (Choose all that apply.)
CorrectIncorrect -
Question 17 of 50
17. Question
Your friend recently heard the flaw in Windows 10 could cause a PC to bluescreen–even when locked–by simply inserting a malicious USB drive. He comes to you for advice on how to eliminate this flaw. Which of the following actions should your friend perform to prevent this type of attack from occurring?
CorrectIncorrect -
Question 18 of 50
18. Question
A hacker works through all possible combinations hoping to guess login credentials correctly. Which type of attack would this BEST be categorized as?
CorrectIncorrect -
Question 19 of 50
19. Question
The workstations in the IT department have been compromised by a hacker and used for DDoS attacks. Which of the following word BEST describes the compromised workstations in the IT department?
CorrectIncorrect -
Question 20 of 50
20. Question
You have just received an email from your bank stating that you need to change the e-banking password by pressing a button that says “Reset your password here”. The password of your e-banking has already been changed a week ago and this email seems suspicious. Which of the following best describes this type of attack?
CorrectIncorrect -
Question 21 of 50
21. Question
After downloading a file from the web, you start noticing your workstation behaving weirdly. Two days later you receive an email from an unknown source stating that the workstation is hacked and now they can use the device to mine for cryptocurrency. Which type of malware MOST likely infected your workstation?
CorrectIncorrect -
Question 22 of 50
22. Question
Your friend Steve worries that if his smartphone is stolen or lost, the sensitive data the phone contains might be exposed to the wrong person. He wants to find a way to secure the device in case of loss. Which of the following is the BEST method of securing the phone?
CorrectIncorrect -
Question 23 of 50
23. Question
Which of the following describes the security method that permits a user to use one set of login credentials — for example, a name and password — to access multiple applications?
CorrectIncorrect -
Question 24 of 50
24. Question
You have been tasked to improve the security of the company’s network infrastructure. The task is to provide a way to authenticate the employees for accessing the corporate wireless network and other network resources before gaining access. Which of the following authentication methods should you implement to complete the task?
CorrectIncorrect -
Question 25 of 50
25. Question
You have been hired to provide a solution to a well-known hotel chain. The hotel manager wants to keep the wireless network open and free for all guests but also wants to prevent people in the neighborhood from accessing it. What will you do to achieve that?
CorrectIncorrect -
Question 26 of 50
26. Question
Which of the following is the LAST step of the seven-step malware removal process according to CompTIA’s best practice procedures?
CorrectIncorrect -
Question 27 of 50
27. Question
You received a trouble ticket from your co-worker, complaining that his workstation is booting up very slowly. He is working on a Windows 10 environment. Which of the following actions should you perform to speed up the boot process on his workstation as fast as possible?
CorrectIncorrect -
Question 28 of 50
28. Question
One of your day-to-day tasks is to run an anti-virus scan on your company’s workstations. If you find out that one of the workstations is infected with malware what action should you perform next according to CompTIA’s best practice procedures for malware removal?
CorrectIncorrect -
Question 29 of 50
29. Question
It has been noticed that the touchscreen on your iPhone doesn’t respond correctly to your touch. Sometimes the touchscreen works sometimes not. Which of the following actions should you perform to possibly solve this issue as soon as possible?
CorrectIncorrect -
Question 30 of 50
30. Question
You are browsing the web and after pressing a click on a well-known website you get the following notification. What sort of threat are you experiencing?
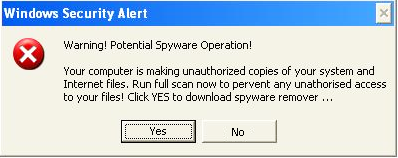 CorrectIncorrect
CorrectIncorrect -
Question 31 of 50
31. Question
Your co-worker Anna just came to you for explanations. Her workstation was infected with malware three (3) days ago. You had removed the malware from her system and the system went back to a normal condition. Today she has the same symptoms as before. Which of the following steps did you forget to follow as part of the CompTIA’s malware removal procedure?
CorrectIncorrect -
Question 32 of 50
32. Question
You’ve been noticed that your smartphone’s battery is draining fast. Even after a full charge, the battery lasts between three (3) and four (4) hours. What actions should you perform to possibly fix this issue as cost-effective as possible? (Choose all that apply.)
CorrectIncorrect -
Question 33 of 50
33. Question
You got an email from Gmail stating that “someone is trying to access your account, check the activity and confirm that was you”. Which of the following threats is this an example of?
CorrectIncorrect -
Question 34 of 50
34. Question
Your co-workers complain about slow network speed whenever they are in the company’s kitchen. Your co-workers use the Wi-Fi in the lobby area without issues. Though the access point (AP) shares the same distance between the kitchen and lobby, the data speed in the former is slower. Which of the following actions should you perform to increase the data speed?
CorrectIncorrect -
Question 35 of 50
35. Question
You receive a trouble ticket from your co-worker, stating that while he was preparing his financial report, all of a sudden his workstation was frozen. What is MOST likely the problem?
CorrectIncorrect -
Question 36 of 50
36. Question
You open Google Chrome, Adobe Illustrator, and the Downloads folder all at once on your workstation. Suddenly, the workstation became unresponsive, and an infinite spinner replaced your mouse cursor. Which of the following actions should you perform to fix the unresponsive system?
CorrectIncorrect -
Question 37 of 50
37. Question
Your close friend Peter is facing an issue with his browser. Each time he types www.google.com on Google Chrome, the URL redirects him to www.malware.com. He cannot find out what’s happening, as the rest of the URLs work perfectly fine. Which of the following does Peter need to do to fix the issue?
CorrectIncorrect -
Question 38 of 50
38. Question
Your co-worker is complaining that his profile keeps getting locked out on his Windows 10 system. Which of the following action is the BEST solution to this problem?
CorrectIncorrect -
Question 39 of 50
39. Question
You see streaking, lines, and missed prints when you are printing documents using your office’s laser printer. What action should you perform next to solve this problem?
CorrectIncorrect -
Question 40 of 50
40. Question
What is the SECOND step of the seven-step malware removal process?
CorrectIncorrect -
Question 41 of 50
41. Question
You just received a new troubleshooting ticket from your co-worker, Peter. He is trying to connect on the internet (wirelessly) but he receives an error message that says “There is an IP address conflict with another system on the network”. Which of the following option will resolve the issue?
CorrectIncorrect -
Question 42 of 50
42. Question
Your smartphone displays a notification stating that a new pair of Bluetooth devices such as headphones have connected to your device without your consent. Which of the following threats is described in this scenario?
CorrectIncorrect -
Question 43 of 50
43. Question
Which of the following protocols and technologies SHOULDN’T be used when you need to connect remotely to another workstation/device/network?
CorrectIncorrect -
Question 44 of 50
44. Question
You have been tasked to increase the security of the company’s server which is running hundreds of virtual machines, including an email server, DHCP server, DNS server, and web server. Which of the following actions should you take to complete the task? (Choose all that apply.)
CorrectIncorrect -
Question 45 of 50
45. Question
You are building a new MySQL database for the payrolls of the IT department. The data type of the primary key in the table is stored as an integer. Which of the following data types would the employee’s name be store in the table?
CorrectIncorrect -
Question 46 of 50
46. Question
You are writing a Python automation script that sends a notification to the network administrator if a port of any switch goes down. Which of the following script file types should the file be in?
CorrectIncorrect -
Question 47 of 50
47. Question
Which of the following is used to help programs know what directory to install files in, where to store temporary files, and where to find user profile settings?
CorrectIncorrect -
Question 48 of 50
48. Question
Which of the following terms is a set of rules applied by the administrator of a network, or website, that restrict the ways in which the network or website may be used by the users and sets guidelines as to how it should be used?
CorrectIncorrect -
Question 49 of 50
49. Question
You have a meeting with a client to discuss the upcoming project. Unfortunately, due to the heavy traffic, you will be late. What should you do?
CorrectIncorrect -
Question 50 of 50
50. Question
What should you do if your cellphone rings while you are working with a customer?
CorrectIncorrect