Time limit: 0
Quiz Summary
0 of 50 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Quiz complete. Results are being recorded.
Results
0 of 50 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the practice exam, but hey, you have unlimited access.😎
Practice makes you perfect! 👊 -
Congratulations! 🥳
You have passed the practice exam successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path. ✌️
Good luck with the exam! Stay strong. 👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 50
1. Question
You are working in a Linux environment and you need to move all files from the subdirectory examsdigest-courses to the current directory. Which of the following command should you type to complete the task?
CorrectIncorrect -
Question 2 of 50
2. Question
Which command on a macOS or Linux system is used to change the permissions of a file?
CorrectIncorrect -
Question 3 of 50
3. Question
“End-of-life” or EOL is a term used by software vendors indicating that it is ending or limiting the support on the product and/or version to shift focus on their newer products and/or version.
CorrectIncorrect -
Question 4 of 50
4. Question
A week ago one of your co-workers plugged a USB into his workstation. The USB was malicious with Trojan scripts inside. As a result, many workstations were affected by that malicious USB. Then, the CEO of the company has announced that access to all USB storage devices should be blocked on all company’s workstations. Which of the following command-line tools should you use to install a new Group Policy to all workstations across the network to disable the use of USB storage devices?
CorrectIncorrect -
Question 5 of 50
5. Question
Your friend Mike asks you how to delete obsolete keys and entries from third-party software on his workstation which is running Windows 10. Which of the following tools should he use to meet the requirement?
CorrectIncorrect -
Question 6 of 50
6. Question
Your co-worker is complaining that every time he turns on his workstation which is running Windows 10, applications such as Dropbox, OneDrive, and Skype loads up. Which of the following commands should he use to disable the program from starting up each time he turns on his workstation?
CorrectIncorrect -
Question 7 of 50
7. Question
You have been tasked to configure the firewall of your company’s network. Your project manager wants to prevent all the web traffic, coming from/to your network. Which of the following ports should you block to prevent the web traffic? (Choose all that apply.)
CorrectIncorrect -
Question 8 of 50
8. Question
Your IT director assigned you a task related to proxy servers. He wants you to educate the junior network engineers about the benefits of using and configuring proxy servers in any organization. Which of the following are the main benefits of using a proxy server? (Choose all that apply.)
CorrectIncorrect -
Question 9 of 50
9. Question
You are on the way to a business meeting outside of your town. You need to connect urgently to the HQ’s network to get some important files that need to be presented at the meeting. Which of the following types of network connections should you use to get the files while heading to the business meeting?
CorrectIncorrect -
Question 10 of 50
10. Question
You know that you won’t use your laptop for an extended period and won’t have an opportunity to charge the battery during that time. Which of the following power modes should you use to save power, but it takes longer to turn back on and resume where the user left off?
CorrectIncorrect -
Question 11 of 50
11. Question
You have three (3) old laptops sitting at your home and you are thinking to give them away to your friends. You want to make sure that all data should be deleted before sharing the laptops. Which of the following data destruction and disposal methods should you execute to allow the data on the drives to be fully destroyed?
CorrectIncorrect -
Question 12 of 50
12. Question
Given the following wireless security protocols and encryption methods, which of the following is the LEAST secure and you have to avoid using it?
CorrectIncorrect -
Question 13 of 50
13. Question
Which of the following physical security measures you should implement in order to protect yourself from shoulder surfing attacks?
CorrectIncorrect -
Question 14 of 50
14. Question
You are setting up a new wireless network in your company’s data center. The wireless network should allow only four (4) devices to be connected and block the rest. The four (4) devices are three (3) wireless cameras and one (1) mobile phone. Based on the requirements provided, which of the following configuration settings should you use to meet the requirement?
CorrectIncorrect -
Question 15 of 50
15. Question
A corporate workstation was recently infected with malware. The malware began to infect other workstations on the same network using the credentials it stole from the first workstation. As a result, the whole network was affected and all devices within the network became unavailable. You have been tasked to find a way to prevent this incident from occurring again. Which of the following actions should you take to prevent this from reoccurring?
CorrectIncorrect -
Question 16 of 50
16. Question
You just got notified that the web server of your company is experiencing a DDoS attack. Twenty (20) internal devices are infected with malware and the cybercriminal uses them to carry out the attack against the web server. Which of the following BEST describes the infected computers?
CorrectIncorrect -
Question 17 of 50
17. Question
A new policy dictates that the employee’s responsibilities will be controlled based on the job functions and tasks within the company. That means, a user account created for pulling records from a database doesn’t need admin rights, while a developer whose main function is updating lines of code doesn’t need access to financial records. Which of the following security concepts is BEST described by this new policy?
CorrectIncorrect -
Question 18 of 50
18. Question
Which of the following would provide the BEST security solution for both computers and smartphones?
CorrectIncorrect -
Question 19 of 50
19. Question
When you are trying to log in to your Facebook account, you are asked to enter your username and password. Which type of authentication method is Facebook using in this case?
CorrectIncorrect -
Question 20 of 50
20. Question
Which of the following security measures should you take to increase the security of physical spaces such as server rooms? (Choose all that apply.)
CorrectIncorrect -
Question 21 of 50
21. Question
ExamsDigest has just set up a new lab consisting of eight (8) laptops four (4) Cisco routers and twelve (12) Cisco switches to allow students to gain hands-on experience using live equipment. The Cisco products are locked in a rack but the laptops are exposed to the public as the lab is open 24/7. Which of the following physical security measures should be used to ensure the laptops are not stolen or moved out of the lab environment?
CorrectIncorrect -
Question 22 of 50
22. Question
You receive a call from the senior network engineer of your company saying that the web server is infected with malware. All the .html, .css, .js and .php files on the server appear to be encrypted and locked. In addition, he received the following warning message asking for bitcoin — as shown in the image below — in order to get the files back:
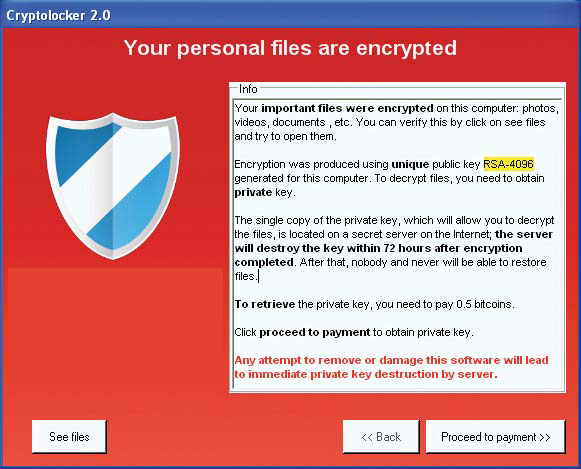
Which type of malware MOST likely infected the web server?
CorrectIncorrect -
Question 23 of 50
23. Question
You are configuring a SOHO (Small Office/Home Office network) router in your home. You want to harden the wi-fi network as much as possible, by using the latest encryption technologies and prevent your neighbors to connect to it. Which of the following actions should you perform to increase the security of your home’s wireless network? (Choose all that apply.)
CorrectIncorrect -
Question 24 of 50
24. Question
Your neighbor’s wireless network was compromised by a hacker who used an attack named brute force attack. The hacker got administrative rights and changed all the default settings inside the wireless access point. Which of the following configurations was most likely used to allow the attack to occur?
CorrectIncorrect -
Question 25 of 50
25. Question
You have been tasked to give the correct type of user accounts to all interns/trainees to have the bare minimum privileges to perform only specific tasks using the company’s workstations. Which of the following types of user accounts should interns/trainees be given to perform their jobs?
CorrectIncorrect -
Question 26 of 50
26. Question
You are trying to update your co-worker’s workstation. Unfortunately, the update can’t be finished, and instead, you get the following error message: “Windows Update cannot currently check for updates because the service is not running.” Which of the following actions should you perform next to solve the issue?
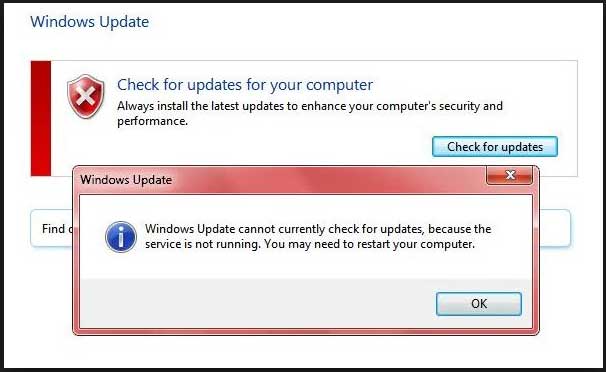 CorrectIncorrect
CorrectIncorrect -
Question 27 of 50
27. Question
You are trying to start your workstation running Windows, and you receive the following error message “Missing Operating System” on the black screen. The message came up after installing a new hard drive on the workstation. Which of the following actions should you perform NEXT to fix the issue?
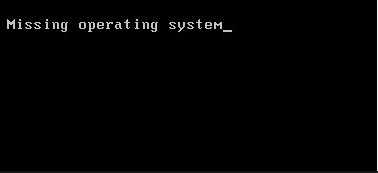 CorrectIncorrect
CorrectIncorrect -
Question 28 of 50
28. Question
You have just identified and confirmed that your co-worker’s system is infected by malware. According to the malware removal procedures, what should you do NEXT to mitigate the risk?
CorrectIncorrect -
Question 29 of 50
29. Question
You may receive a message popping up on certain websites when using Microsoft IE that says “The security certificate has expired or is not yet valid“. Which of the following settings needs to be changed on your workstation to fix the error?
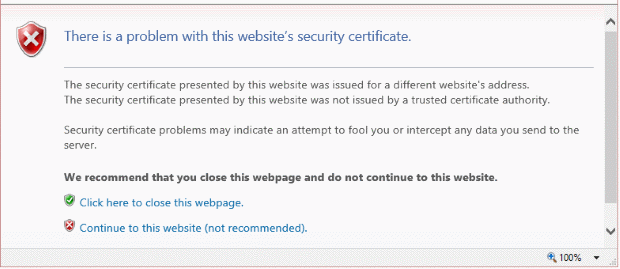 CorrectIncorrect
CorrectIncorrect -
Question 30 of 50
30. Question
A cyber-attacker send a message from the victim’s account to their bank and instruct them to transfer funds to the attacker’s bank account. What type of attack is described in this scenario?
CorrectIncorrect -
Question 31 of 50
31. Question
Assuming that someone might be listening to your daily conversations with your peers when your smartphone is in your pocket. Which of the following threats is this an example of?
CorrectIncorrect -
Question 32 of 50
32. Question
Your smartphone displays a notification stating that a new pair of Bluetooth devices such as headphones have connected to your device without your consent. Which of the following threats is described in this scenario?
CorrectIncorrect -
Question 33 of 50
33. Question
Peter’s smartphone network connection works fine when he is at the company or at his neighbor’s place, but when he is at home, then he has limited bandwidth and the internet is extremely slow. Peter needs your help to troubleshoot this issue. What is the FIRST step you should take?
CorrectIncorrect -
Question 34 of 50
34. Question
Which of the following is most likely the issue when a smartphone gets very hot and the battery is draining fast?
CorrectIncorrect -
Question 35 of 50
35. Question
You just received a new troubleshooting ticket from your co-worker, Peter. He is trying to connect on the internet (wirelessly) but he receives an error message that says “There is an IP address conflict with another system on the network”. Which of the following option will resolve the issue?
CorrectIncorrect -
Question 36 of 50
36. Question
Which of the following regulations applies when processing personal data within the European Union?
CorrectIncorrect -
Question 37 of 50
37. Question
Your co-worker, David, is facing some issues with the antivirus and needs your help to resolve it as soon as possible. Putting in mind that his workstation is running Windows 10, which of the following technologies would BEST allow you to remotely access his computer and fix the antivirus issue?
CorrectIncorrect -
Question 38 of 50
38. Question
You are worried about power fluctuations that may occur and cause power spike damage to your switch rack cabinet. Which of the following appliances will you use to eliminate this issue?
CorrectIncorrect -
Question 39 of 50
39. Question
You are setting up your new online shop, selling courses in your niche. The payment gateway is built on top of Stripe and PayPal. Which of the following compliance types should you be MOST concerned within dealing with credit cards?
CorrectIncorrect -
Question 40 of 50
40. Question
Which of the following terms refers to the order and manner in which physical or electronic evidence in criminal and civil investigations is being handled?
CorrectIncorrect -
Question 41 of 50
41. Question
Your friend David is learning the new graphic design tools from Adobe by watching videos on YouTube. Your friend is willing to pay for a license to be able to use Photoshop and Illustrator. Which of the following type of licenses would you recommend to your friend?
CorrectIncorrect -
Question 42 of 50
42. Question
You have been tasked to replace a power supply in a desktop computer. Which of the following actions should you take FIRST?
CorrectIncorrect -
Question 43 of 50
43. Question
You have been tasked to repair ten (10) workstations. Which of the following actions should you take FIRST?
CorrectIncorrect -
Question 44 of 50
44. Question
Υou are working on very sensitive electronic equipment and you want to prevent the buildup of static electricity on your body, which can result in electrostatic discharge. Which of the following device will you use to safely ground yourself and prevent this from happening?
CorrectIncorrect -
Question 45 of 50
45. Question
You are working on upgrading the RAM and Hard drive on your laptop. After removing the old components from the laptop, where should you safely store them?
CorrectIncorrect -
Question 46 of 50
46. Question
Your manager asks you to recommend a device that is able to supply power to electrical equipment during a power outage for a certain amount of time. Which of the following devices should you recommend?
CorrectIncorrect -
Question 47 of 50
47. Question
You are working with a network designer to build a new network for a client. The project requires to configure one (1) Router, two (2) firewalls, one (1) Mail Server, and one (1) Web Server. He presents the following diagram to get the overall idea of the outcome. What type of diagram did the network designer represent to you?
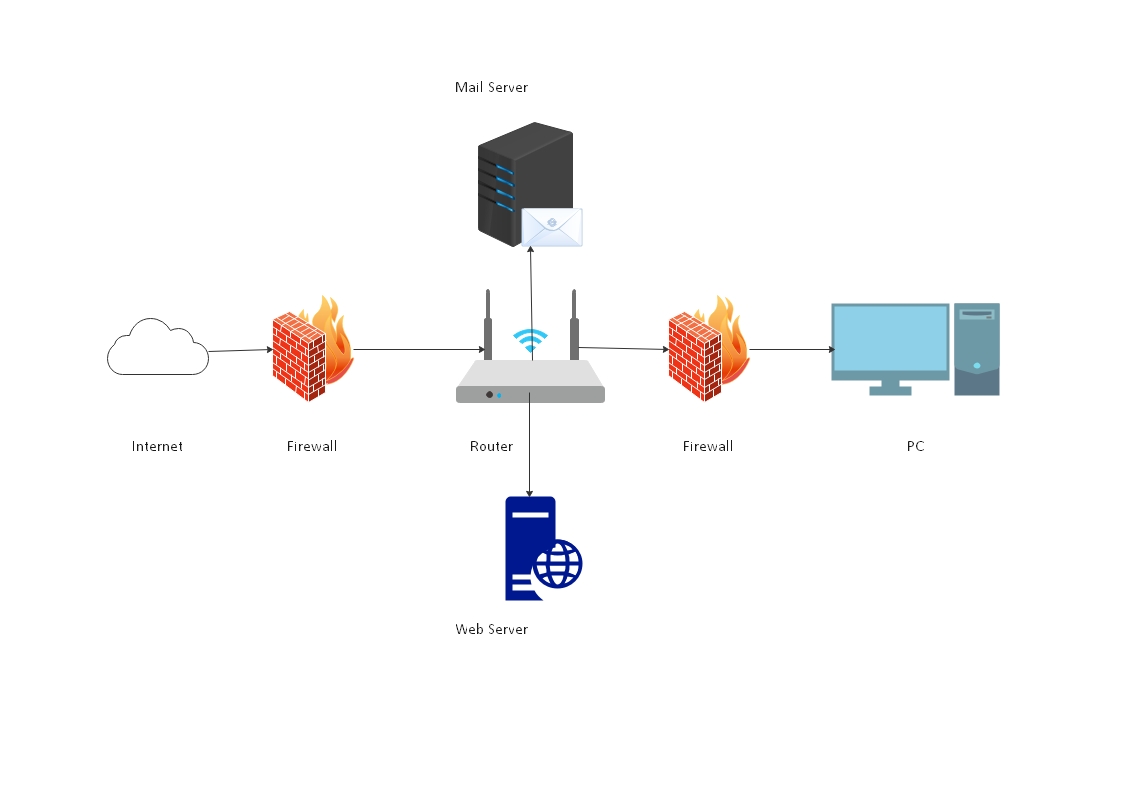 CorrectIncorrect
CorrectIncorrect -
Question 48 of 50
48. Question
A hacker works through all possible combinations hoping to guess login credentials correctly. Which type of attack would this BEST be categorized as?
CorrectIncorrect -
Question 49 of 50
49. Question
You have recently been hired as an IT security specialist by a small company to improve the security of their wireless network. You have been tasked to harden the wireless network infrastructure to the highest possible level. Which of the following protocol encryption methods should you implement for the BEST security? (Choose all that apply.)
CorrectIncorrect -
Question 50 of 50
50. Question
Your laptop is running Windows 10 and starts getting slower and slower over time. After a quick investigation, you notice that the CPU utilization is between 85% and 95%. Then you start closing open applications to drop the CPU utilization. Unfortunately, the next day the issue with the CPU utilization happens again. Which of the following tools can you use to check the CPU utilization on Windows 10?
CorrectIncorrect