Time limit: 0
Quiz Summary
0 of 30 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Quiz complete. Results are being recorded.
Results
0 of 30 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the quiz, but hey, you have unlimited access.😎
Practice makes you perfect! 👊 -
Congratulations! 🥳
You have passed the quiz successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path.✌️
Good luck with the exam! Stay strong.👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 30
1. Question
A company signs up a new contract with an Internet service provider (ISP). The ISP presents a document which states that the company agrees to adhere to stipulations such as:
Not using the service as part of violating any law Not attempting to break the security of any computer network or user Not posting commercial messages to Usenet groups without prior permission Not attempting to send junk e-mail or spam to anyone who doesn't want to receive it Not attempting to mail bomb a site with mass amounts of e-mail in order to flood their server
Which of the following documents is described in the above scenario?
CorrectIncorrect -
Question 2 of 30
2. Question
An author just published his new eBook on Amazon but he worries about copyright issues as the previous eBook was found on file-sharing websites without his permission. The author wants to prevent users from sharing his content online. Which of the following tools allows the author to prevent unauthorized use of his content?
CorrectIncorrect -
Question 3 of 30
3. Question
A cybersecurity analyst follows an incident response plan to remediate a threat. Which of the following actions the analyst should perform NEXT as part of the recovery process after eradicating the malware from the victimized system?
CorrectIncorrect -
Question 4 of 30
4. Question
The process of replacing HTML control characters (e.g. , “, &, etc) into their encoded representatives (e.g. “& lt ;” “& gt ;” “& quot ;” “& amp ;” etc..) is known as?
CorrectIncorrect -
Question 5 of 30
5. Question
Your company is using Wireshark as a network protocol analyzer. The workstation with an IP address of 192.168.0.6 consumes too much bandwidth from the network without an obvious reason. Which of the following filters should you use to display packets to or from the IP address of 192.168.0.6?
CorrectIncorrect -
Question 6 of 30
6. Question
Your co-worker Marie sent you the following screenshot. She states that each time she opens her workstation the usage of the RAM reaches 90% – 99% and the error “Your computer is low on memory” popping up. Which of the following might be the cause of high memory usage? (Choose all that apply.)
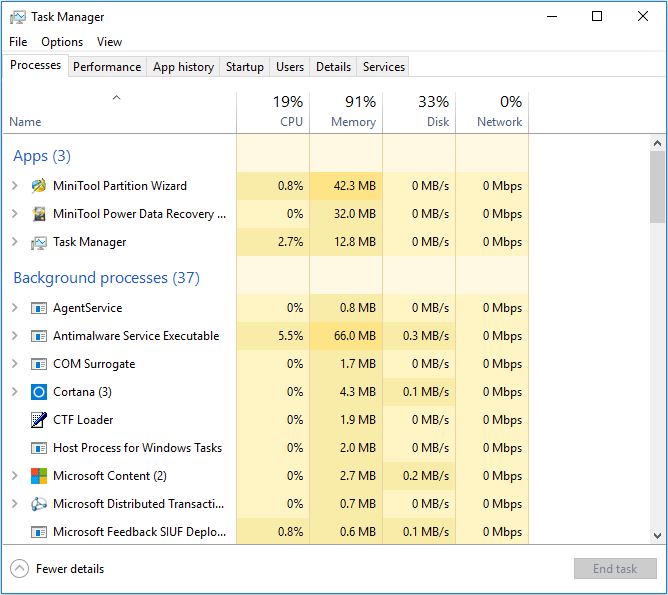 CorrectIncorrect
CorrectIncorrect -
Question 7 of 30
7. Question
Students at examsdigest.com login using their username and password. As this method has security issues, ExamsDigest’s team looking for solutions to increase the security of the login system by requiring students to provide more evidence to prove their identity. Which of the following authentication methods does ExamsDigest need to implement?
CorrectIncorrect -
Question 8 of 30
8. Question
The private IP range of the accounting department is 192.168.0.5 – 192.168.0.10. The hosts with IP address 192.168.0.7 and 192.168.0.9 aren’t able to connect to examsdigest.com by its domain name but only by its public IP address (145.34.2.7). Which of the following tools should you use to find out if these hosts have opened port 54?
CorrectIncorrect -
Question 9 of 30
9. Question
You are conducting a log review scan to detect the users who have been locked out from their accounts in order to proceed to the recovery stage. Which of the following sources of information would provide you with the most accurate information for you to use in determining who has been locked out or not?
CorrectIncorrect -
Question 10 of 30
10. Question
The developers of your company for efficiency purposes they need to implement a solution to deploy new code releases automatically into the production environment. Which of the following software development method the developers should implement?
CorrectIncorrect -
Question 11 of 30
11. Question
You have been tasked to improve the wired network security of the company’s network by limiting the number of MAC addresses on a given port. Packets that have a matching MAC address should be considered secure packets and should be forwarded; all other packets (unsecured packets) should be restricted. Which of the following features should you implement to complete the task?
CorrectIncorrect -
Question 12 of 30
12. Question
A penetration tester performing a pentest on the network of the Acme corporation. Once he tried to connect to the network the IPS/IDS system blocked his workstation, as it appeared a suspicious device. Which of the following features should the company use to allow the pentester to continue his work.
CorrectIncorrect -
Question 13 of 30
13. Question
Given the following injection attacks, which one allows an attacker to interfere with the queries that an application makes to its database?
CorrectIncorrect -
Question 14 of 30
14. Question
A developer is building a new CRUD application for a university. The path like
university.com/students/2/course/6accessing the course with id 6 for the student with id 2. This is an example of which service-oriented architecture?CorrectIncorrect -
Question 15 of 30
15. Question
The developer team of your company has just released a new social media app. The next task for the team is to measure the robustness of the new app under extremely heavy load conditions to ensure that the app doesn’t crash under crunch situations. Which of the following software assessment actions do they need to follow to complete the task?
CorrectIncorrect -
Question 16 of 30
16. Question
Your company is using a Web Vulnerability Scanner tool named Acunetic to check whether your website and web applications are vulnerable. While you were reviewing a scan report you saw the following URL:
http://test.webarticles.com/show.asp?view=../../../../../Windows/system.ini HTTP/1.1What type of attack is conducted on that website?
CorrectIncorrect -
Question 17 of 30
17. Question
Α company is planning to increase the security of its private network by adding a new security device between the public and its private network. The device will be used as a proxy server and will be responsible for routing the traffic between the two networks. Which of the following devices should be installed to isolate access to the internal network?
CorrectIncorrect -
Question 18 of 30
18. Question
Your organization is working with a contractor to build a database. You need to find a way to hide the actual data from being exposed to the contractor. Which of the following technique will you use in order to allow the contractor to test the database environment without having access to actual sensitive customer information?
CorrectIncorrect -
Question 19 of 30
19. Question
Your company has moved any workload from its on-premises environment to Amazon Web Services (AWS) to benefit from substantial IT costs savings, business agility, and operational resilience. You have been tasked to recommend a tool that enables security posture assessment of cloud environments. Which of the following tools should you recommend to complete the task?
CorrectIncorrect -
Question 20 of 30
20. Question
The software that monitors user activity and automatically prevents malware between cloud service users and cloud applications is known as:
CorrectIncorrect -
Question 21 of 30
21. Question
The developer of your company wrote the following code snippet in Java to show the account numbers and balances for the current user’s id as provided in a URL.
String accountBalanceQuery = "SELECT accountNumber, balance FROM accounts WHERE account_owner_id = " + request.getParameter("user_id"); Statement statement = connection.createStatement(); ResultSet rs = statement.executeQuery(accountBalanceQuery); while (rs.next()) { page.addTableRow(rs.getInt("accountNumber"), rs.getFloat("balance")); }Under normal operation, the user with ID 4 might be logged in, and visit the URL: https://mybank.ebanking/show_balances?user_id=4. This means that accountBalanceQuery would end up being:
SELECT accountNumber, balance FROM accounts WHERE account_owner_id = 4A cyber security criminal changed the parameter “user_id” to be interpreted as:
0 OR 1=1When this query is passed to the database, it returned all the account numbers and balances it has stored, and rows are added to the page to show them. The attacker now knows every user’s account numbers and balances. Which of the following type of attacks is conducted against the website?
CorrectIncorrect -
Question 22 of 30
22. Question
Which of the following types of disaster recovery sites allows a company to continue normal business operations, within a very short period of time after a disaster?
CorrectIncorrect -
Question 23 of 30
23. Question
A cybersecurity researcher is debugging a code by examining the source code of the application before the execution. Which of the following code analysis methods the researcher is currently performing?
CorrectIncorrect -
Question 24 of 30
24. Question
A new social media app was launched recently that accepts all users worldwide by default. A cybersecurity analyst after reviewing the firewall logs detects that users from specific countries have conducted a cyber attack on the app. Which of the following access control method should the analyst recommend to the developers?
CorrectIncorrect -
Question 25 of 30
25. Question
During a vulnerability scan, you found a serious SQL injection vulnerability in one of your online shop that has 10,000 daily visitors. The eshop provides 99.999% availability to customers so it can’t be taken offline to fix the SQL injection vulnerability. Which of the following solutions should you recommend to the eshop administrators until the eshop can be remediated?
CorrectIncorrect -
Question 26 of 30
26. Question
The developer of your company just released a new version of the registration form on the web application. Now the username field should contain only characters and the password field accepts special characters and numbers. This an example of which secure coding best practices?
CorrectIncorrect -
Question 27 of 30
27. Question
Mike’s organization uses a hybrid approach for its infrastructure as they have an on-premise environment for their services but also they use Amazon Web Services for other services. Which of the following software tools do they need to ensure that network traffic between on-premises devices and the cloud provider complies with the organization’s security policies?
CorrectIncorrect -
Question 28 of 30
28. Question
If an employee tried to forward a business email outside the corporate domain or upload a corporate file to a consumer cloud storage service like Google drive, the employee would be denied permission. Which of the following process is described in the above scenario?
CorrectIncorrect -
Question 29 of 30
29. Question
You just completed an HPING scan and received the following output:
HPING 4.2.2.1 (eth1 4.2.2.1): S set, 40 headers + 0 data bytes len=46 ip=4.2.2.1 ttl=56 DF id=32839 sport=50 flags=RA seq=0 win=0 rtt=264.3 ms len=46 ip=4.2.2.1 ttl=56 DF id=32840 sport=51 flags=RA seq=1 win=0 rtt=277.6 ms len=46 ip=4.2.2.1 ttl=56 DF id=32841 sport=52 flags=RA seq=2 win=0 rtt=285.4 ms len=46 ip=4.2.2.1 ttl=56 DF id=32842 sport=53 flags=SA seq=3 win=49312 rtt=270.7 ms len=46 ip=4.2.2.1 ttl=56 DF id=32843 sport=54 flags=RA seq=4 win=0 rtt=225.1 ms len=46 ip=4.2.2.1 ttl=56 DF id=32844 sport=55 flags=RA seq=5 win=0 rtt=202.6 ms len=46 ip=4.2.2.1 ttl=56 DF id=32845 sport=56 flags=RA seq=6 win=0 rtt=196.7 msBased on these results, which of the following services returned an SYN-ACK?
CorrectIncorrect -
Question 30 of 30
30. Question
Which of the following statements describes the difference between the Red team and the Blue team in a cybersecurity testing exercise?
CorrectIncorrect