Quiz 1 of 0
Exam simulator: Hardware and Network Troubleshooting
Anastasia-Instructor August 28, 2022
Time limit: 0
Quiz Summary
0 of 15 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Quiz complete. Results are being recorded.
Results
0 of 15 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the practice exam, but hey, you have unlimited access.😎
Practice makes you perfect! 👊 -
Congratulations! 🥳
You have passed the practice exam successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path. ✌️
Good luck with the exam! Stay strong. 👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 15
1. Question
Next to each protocol type the port that it uses to function.
-
Protocol Port SSH DNS SMTP FTP HTTP HTTPS
CorrectIncorrect -
-
Question 2 of 15
2. Question
You have been tasked to create a new Access Control List on the company’s firewall to prevent any HTTP traffic from/to the network. Type the port number that needs to be added to the ACL rule.
-
ACL rule: access-list 100 deny tcp any any eq
CorrectIncorrect -
-
Question 3 of 15
3. Question
Drag and drop the various 802.11 wireless standards into the frequencies they use.
Sort elements
- 802.11g
- 802.11a
- 802.11n
-
2.4 GHz
-
5 GHz
-
2.4 GHz / 5 GHz
CorrectIncorrect -
Question 4 of 15
4. Question
Sort the steps to resolve problems according to CompTIA troubleshooting methodology.
-
Verify full system functionality and, if applicable, implement preventive measures
-
Establish a plan of action to resolve the problem and implement the solution
-
Establish a theory of probable cause (question the obvious)
-
Test the theory to determine cause
-
Identify the problem
-
Document findings, actions, and outcomes
View Answers:
CorrectIncorrect -
-
Question 5 of 15
5. Question
Given the following Pentium 4 motherboard, match the missing parts with the name of the components.
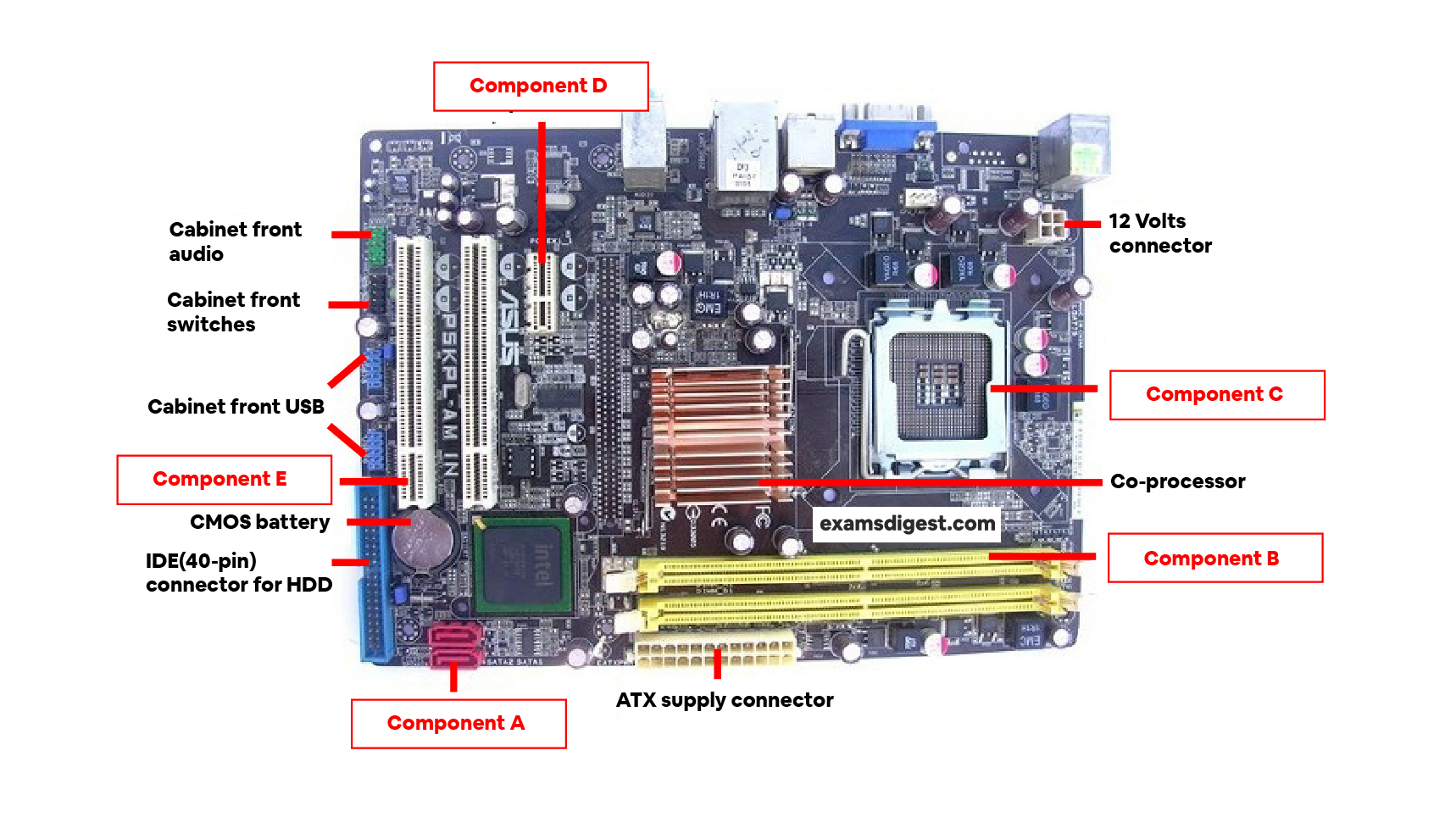
Sort elements
- SATA-ports
- Memory (RAM) slots
- Processor socket
- PCI express slot
- PCI slots
-
Component A
-
Component B
-
Component C
-
Component D
-
Component E
CorrectIncorrect -
Question 6 of 15
6. Question
Drag and drop the name of the common connector types into their respective places.
Sort elements
- BNC connector
- RJ-11
- USB-C
- RJ-45
CorrectIncorrect -
Question 7 of 15
7. Question
Drag and drop the name of the common networking tools into their respective places.
Sort elements
- Multimeter
- Crimper
- Cable tester
- Punchdown tool
CorrectIncorrect -
Question 8 of 15
8. Question
Drag and drop the name of the common networking hardware devices into their respective places.
Sort elements
- Router
- Access point
- Switch
- Firewall
-
A networking device that forwards data packets between computer networks
-
A device that creates a wireless local area network
-
Connects devices (such as computers and printers) in a network to each other
-
A device that monitors incoming and outgoing network traffic and permits or blocks data packets based on a set of security rules
CorrectIncorrect -
Question 9 of 15
9. Question
Drag and drop the name of the protocol into their respective TCP/UDP port numbers.
Sort elements
- SLP
- DHCP
- SNMP
- RDP
-
Port 427
-
Port 67
-
Port 162
-
Port 3389
CorrectIncorrect -
Question 10 of 15
10. Question
Given the following firewall configuration requirements, type the correct port number to complete the access control rules.
-
Firewall configuration requirement #1: Allow SSH connections but prevent Telnet connections.
Rule #1: access-list 100 allow tcp eq deny tcp eq
Firewall configuration requirement #2: Allow HTTPS traffic but prevent HTTP traffic from/to the network.
Rule #2: access-list 100 allow tcp eq deny tcp eq
CorrectIncorrect -
-
Question 11 of 15
11. Question
Drag and drop the name of the common cloud models into their respective places.
Sort elements
- IaaS
- PaaS
- SaaS
- Public cloud
-
Offer services such as pay-as-you-go storage, networking, and virtualization
-
Provides hardware and software tools over the internet, and people use these tools to develop applications
-
Make software available to users over the internet, usually for a monthly subscription fee
-
A type of computing in which a service provider makes resources available to the public via the internet
CorrectIncorrect -
Question 12 of 15
12. Question
Drag and drop the TCP/UDP port numbers into their respective protocol name.
Sort elements
- Port 80
- Port 548
- Port 110
- Port 23
-
HTTP
-
AFP
-
POP3
-
Telnet
CorrectIncorrect -
Question 13 of 15
13. Question
You have been tasked to create a new Access Control List on the company’s firewall to prevent any FTP access to the webserver and permit any SSH access to the webserver.
Type the port numbers that need to be added to the ACL rule to complete the task.
-
ACL rule: access-list 100 deny tcp any any eq
ACL rule: access-list 100 permit tcp any any eq
CorrectIncorrect -
-
Question 14 of 15
14. Question
Given the following firewall configuration requirements, type the correct port number to complete the access control rules.
-
Firewall configuration requirement #1: Allow SMTP and POP3 traffic but prevent IMAP.
Rule #1: access-list 100 allow tcp eq allow tcp eq deny tcp eq
Firewall configuration requirement #2: Allow the DNS server to resolve domain names and prevent DHCP requests from the network.
Rule #2: access-list 100 allow tcp eq deny udp eq
CorrectIncorrect -
-
Question 15 of 15
15. Question
Next to each protocol type the port that it uses to function.
-
Protocol Port POP3 IMAP RDP SLP AFP LDAP
CorrectIncorrect -







