Time limit: 0
Quiz Summary
0 of 15 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Quiz complete. Results are being recorded.
Results
0 of 15 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the quiz, but hey, you have unlimited access.😎
Practice makes you perfect! 👊 -
Congratulations! 🥳
You have passed the quiz successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path.✌️
Good luck with the exam! Stay strong.👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 15
1. Question
Which of the following categories would contain information that can be used to identify a specific individual such as social security numbers and phone numbers?
CorrectIncorrect -
Question 2 of 15
2. Question
Your co-worker Jax is constantly complaining about the slow network performance on his workstation. Which of the following are common activities that cause bandwidth problems on Jax’s network? (Choose all that apply.)
CorrectIncorrect -
Question 3 of 15
3. Question
One station on the network notifies the other station on the network in a ring fashion when they are not receiving the transmission signals with the aim of self-repairing network problems. This process is known as?
CorrectIncorrect -
Question 4 of 15
4. Question
An information system which is so critical to an organization that in case of corruption or loss of access to it would have a serious impact on the organization’s ability to conduct business is known as?
CorrectIncorrect -
Question 5 of 15
5. Question
The private IP range of the accounting department is 192.168.0.5 – 192.168.0.10. The hosts with IP address 192.168.0.7 and 192.168.0.9 aren’t able to connect to examsdigest.com by its domain name but only by its public IP address (145.34.2.7). Which of the following tools should you use to find out if these hosts have opened port 54?
CorrectIncorrect -
Question 6 of 15
6. Question
Your company is using Wireshark as a network protocol analyzer. The workstation with an IP address of 192.168.0.6 consumes too much bandwidth from the network without an obvious reason. Which of the following filters should you use to display packets to or from the IP address of 192.168.0.6?
CorrectIncorrect -
Question 7 of 15
7. Question
Which of the following categories would contain information about an individual’s demographic information, medical histories, laboratory results, and mental health conditions?
CorrectIncorrect -
Question 8 of 15
8. Question
A company follows the data retention policy as it is a framework of rules for holding, storing, and deleting the information it generates. The company’s policy states the accounting-related data is stored for a period of 3 years before the permanent deletion. Which of the following process does the company follow to destroy the data?
CorrectIncorrect -
Question 9 of 15
9. Question
The IT team of a company has just implemented a bandwidth monitoring solution to identify alarming and sudden network spikes in their network traffic. What might be the cause of the unusual network spikes in their network? (Choose all that apply.)
CorrectIncorrect -
Question 10 of 15
10. Question
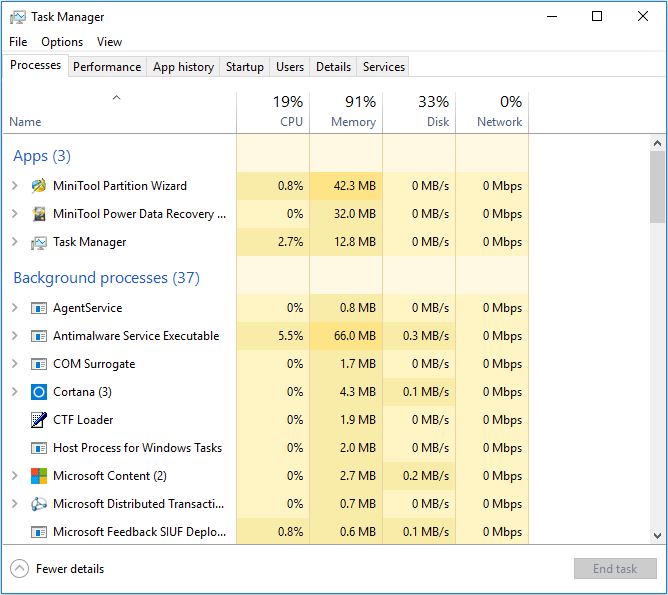
Your co-worker Marie sent you the following screenshot. She states that each time she opens her workstation the usage of the RAM reaches 90% – 99% and the error “Your computer is low on memory” popping up. Which of the following might be the cause of high memory usage? (Choose all that apply.)
 CorrectIncorrect
CorrectIncorrect -
Question 11 of 15
11. Question
You have been hired to investigate an activity from an attacker who compromised a host on the company’s network. The attacker used credentials from an employee to breach the system. After a while, he gained access to a Linux server and he started using
sudocommands to perform malicious activities. What sort of attack the attacker used?CorrectIncorrect -
Question 12 of 15
12. Question
A cybersecurity analyst follows an incident response plan to remediate a threat. Which of the following actions the analyst should perform NEXT as part of the recovery process after eradicating the malware from the victimized system?
CorrectIncorrect -
Question 13 of 15
13. Question
Wireshark is a command-line utility that allows you to capture and analyze network traffic going through your system. It is often used to help troubleshoot network issues, as well as a security tool. (True/False)
CorrectIncorrect -
Question 14 of 15
14. Question
Which of the following process describes how long businesses need to keep a piece of information (a record), where it’s stored, and how to dispose of the record when its time?
CorrectIncorrect -
Question 15 of 15
15. Question
Which of the following categories would contain information about an individual’s biometric data, genetic information, and sexual orientation?
CorrectIncorrect