Time limit: 0
Quiz Summary
0 of 40 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Quiz complete. Results are being recorded.
Results
0 of 40 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the quiz, but hey, you have unlimited access.😎
Practice makes you perfect! 👊 -
Congratulations! 🥳
You have passed the quiz successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path.✌️
Good luck with the exam! Stay strong.👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 40
1. Question
Multifactor authentication combines two or more independent credentials: what the user knows (password), what the user has (security token) and what the user is (biometric verification). True or False?
CorrectIncorrect -
Question 2 of 40
2. Question
Which of the following servers is used in 802.1X-based networks to authenticate users?
CorrectIncorrect -
Question 3 of 40
3. Question
A technician is called to block certain computers from connecting to the Wi-Fi network. The computers that need to be blocked have the following MAC addresses:
- Computer A: 00:00:5e:00:53:af
- Computer B: aa:55:5e:00:53:af
- Computer C: 44:20:5e:00:53:af
Which of the following tools does the technician need to complete the task?
CorrectIncorrect -
Question 4 of 40
4. Question
Drag and drop the common networking attacks into their respective fields.
Sort elements
- Social engineering
- Rogue access point
- Evil twin
-
Uses psychological manipulation to trick users into making security mistakes or giving away sensitive information.
-
Any unauthorized WLAN radio that is connected to a corporate network.
-
A fake Wi-Fi network that looks like a legitimate access point to steal victims’ sensitive details.
CorrectIncorrect -
Question 5 of 40
5. Question
One purpose of a brute-force attack is to:
CorrectIncorrect -
Question 6 of 40
6. Question
Exploits are a weakness in software systems, while vulnerabilities are attacks made to take advantage of exploits.
CorrectIncorrect -
Question 7 of 40
7. Question
Which of the following networking attacks redirects online traffic to a fraudulent website that resembles its intended destination?
CorrectIncorrect -
Question 8 of 40
8. Question
Which of the following attacks doesn’t require the use of technology in order to get access to sensitive data?
CorrectIncorrect -
Question 9 of 40
9. Question
Which one of the following attacks requires the attacker to be on the same network as the victim?
CorrectIncorrect -
Question 10 of 40
10. Question
Which of the following passwords you would choose to make your account harder to be hacked? (Select TWO)
CorrectIncorrect -
Question 11 of 40
11. Question
Which of the following represents an authorized simulated attack on a system with the purpose of identifying weak spots that attackers could take advantage of?
CorrectIncorrect -
Question 12 of 40
12. Question
Which of the following statements are true regarding Security Information and Event Management (SIEM)? (Select TWO)
CorrectIncorrect -
Question 13 of 40
13. Question
Which of the following process comprises scanning devices on a network for missing software updates and keeping the devices updated to avoid security threats?
CorrectIncorrect -
Question 14 of 40
14. Question
Which of the following security concepts is a dictionary that provides definitions for publicly disclosed cybersecurity vulnerabilities and exposures?
CorrectIncorrect -
Question 15 of 40
15. Question
A graduate intern asked you to explain to him what is zero-day vulnerability all about. Which of the following statements is true?
CorrectIncorrect -
Question 16 of 40
16. Question
A network technician is tasked with implementing a solution to increase the local area network security within an organization. All of the company’s external-facing servers (Web server, FTP server) should be placed in a separate area in order to be accessible from the internet, and the rest servers (Mail server, Storage server) of the internal LAN to be unreachable. Which of the following techniques does the technician need to implement to meet the requirement?
CorrectIncorrect -
Question 17 of 40
17. Question
A network security engineer is tasked with implementing a solution to allow users from untrusted networks to access the Web Server and the Mail Server while keeping the private network secured and inaccessible. Which of the following does the engineer need to implement to complete the task?
CorrectIncorrect -
Question 18 of 40
18. Question
Which of the following options are considered authentication protocols? (Select TWO)
CorrectIncorrect -
Question 19 of 40
19. Question
Which of the following is used in a distributed denial-of-service (DDoS) attack?
CorrectIncorrect -
Question 20 of 40
20. Question
In which of the following API attacks does the attacker intercept communications between an API endpoint and a client in order to steal and/or alter the confidential data that is passed between them?
CorrectIncorrect -
Question 21 of 40
21. Question
Your website uses Cloudflare to resolve DNS queries. Upon checking the records, you have discovered there are A and MX record entries that point to unknown and potentially harmful IP addresses. Which of the following attacks have you just discovered?
CorrectIncorrect -
Question 22 of 40
22. Question
A hacker introduces corrupt Domain Name System (DNS) data into a DNS resolver’s cache to redirect users either to the wrong websites or to his own computer. What type of DNS attack does the hacker implement in this scenario?
CorrectIncorrect -
Question 23 of 40
23. Question
A security expert is tasked with implementing a solution to prevent Rogue DHCP servers from offering IP addresses to end-users within an organization. Which of the following security technology does the expert need to implement to meet the requirement?
CorrectIncorrect -
Question 24 of 40
24. Question
In which of the following wireless network attacks does the attacker set up a fraudulent Wi-Fi access point that appears to be legitimate but is used to eavesdrop on wireless communications?
CorrectIncorrect -
Question 25 of 40
25. Question
In which of the following types of malware does an attacker prevent users from accessing their system or personal files and demand a ransom payment in order to regain access?
CorrectIncorrect -
Question 26 of 40
26. Question
An attacker breaks into a password-protected computer by systematically entering every word in a dictionary as a password. What type of attack does the attacker carry out?
CorrectIncorrect -
Question 27 of 40
27. Question
An attacker impersonates a delivery driver and waits outside of a building. When an employee gains security’s approval and opens the door, the attacker asks the employee to hold the door to gain access to the building. What type of social engineering attack the attacker has performed?
CorrectIncorrect -
Question 28 of 40
28. Question
A cybercriminal stole the personal information or confidential information of a victim by peering over the target’s shoulders. What type of attack did the cybercriminal perform?
CorrectIncorrect -
Question 29 of 40
29. Question
A technician is tasked with improving the wired network security within an organization by limiting the number of MAC addresses on a given port. Packets that have a matching MAC address should be considered secure packets and should be forwarded; all other packets (unsecured packets) should be restricted. Which of the following features does the technician need to implement to complete the task?
CorrectIncorrect -
Question 30 of 40
30. Question
You have been tasked with implementing a solution to send product offers to consumers’ smartphones when they trigger a search in a particular geographic location, enter a mall, neighborhood, or store. What solution will you implement in order to achieve that?
CorrectIncorrect -
Question 31 of 40
31. Question
Which of the following VPN solutions is used to connect two local area networks utilized by businesses that want to provide their employees secure access to network resources?
CorrectIncorrect -
Question 32 of 40
32. Question
A network administrator is tasked with accessing a remote computer to handle some administrative tasks over an unsecured network in a secure way. Which of the following protocols does the administrator need to use to connect to the device?
CorrectIncorrect -
Question 33 of 40
33. Question
The attacker uses a tool named Driftnet to fool both router and workstation to connect to the attacker’s machine, instead of to each other. Then, the attacker is secretly in the middle of all communications. What type of attack is this an example of?
CorrectIncorrect -
Question 34 of 40
34. Question
Which of the following protocols is used in the AAA framework to provide centralized authentication for users who want to gain access to the network?
CorrectIncorrect -
Question 35 of 40
35. Question
An administrator is tasked with implementing a solution that will provide limited capabilities (such as browsing) to guest Wi-Fi users while keeping the rest of the user roles untouched. Which of the following technologies does the administrator need to implement?
CorrectIncorrect -
Question 36 of 40
36. Question
End-users within an office building report web server connectivity issues. A network administrator troubleshooting the issue notices there is a high CPU load on the server when typing the
grep processor /proc/cpuinfocommand. Which of the following is causing the issue?CorrectIncorrect -
Question 37 of 40
37. Question
A rogue postal worker sits in a post office and intercepts letters written between two people. This postal worker can read private messages and even edit the contents of those letters before passing them along to their intended recipients. What type of attack is this an example of?
CorrectIncorrect -
Question 38 of 40
38. Question
Drag and drop the social engineering attacks into their respective fields.
Sort elements
- Phishing
- Tailgating
- Shoulder surfing
-
An attack that uses masquerade email as a means of taking advantage of users
-
A type of attack in which someone without the proper authentication follows an authenticated employee into a restricted area
-
A type of data theft where cybercriminals steal personal information or confidential information by peering over the target’s shoulders
CorrectIncorrect -
Question 39 of 40
39. Question
Which of the following is the MOST effective way to prevent network security breaches from happening in the workplace?
CorrectIncorrect -
Question 40 of 40
40. Question
Which of the following types of attacks is shown in the figure below?
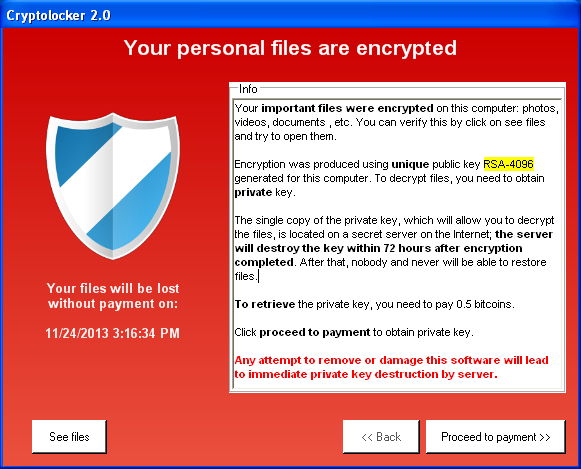 CorrectIncorrect
CorrectIncorrect