Time limit: 0
Quiz Summary
0 of 10 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Quiz complete. Results are being recorded.
Results
0 of 10 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the quiz, but hey, you have unlimited access.😎
Practice makes you perfect! 👊 -
Congratulations! 🥳
You have passed the quiz successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path.✌️
Good luck with the exam! Stay strong.👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 10
1. Question
Which of the following type of contracts is designed to outline the requirements of confidential materials, knowledge, or information between two or more parties for a certain purpose?
CorrectIncorrect -
Question 2 of 10
2. Question
A penetration tester is conducting a pen test for a company. During the initial planning phase, the company documents 4 servers as targets for the penetration test. The penetration tester after scanning the network identified one more server that wasn’t in the planning phase. Then he asked the project manager of the company if this server needs to be assessed and he replied in the affirmative. Which of the following describes the above scenario?
CorrectIncorrect -
Question 3 of 10
3. Question
Which of the following disclaimers should be included in the following penetration testing agreement between the penetration tester and the business owner? (Choose all that apply.)
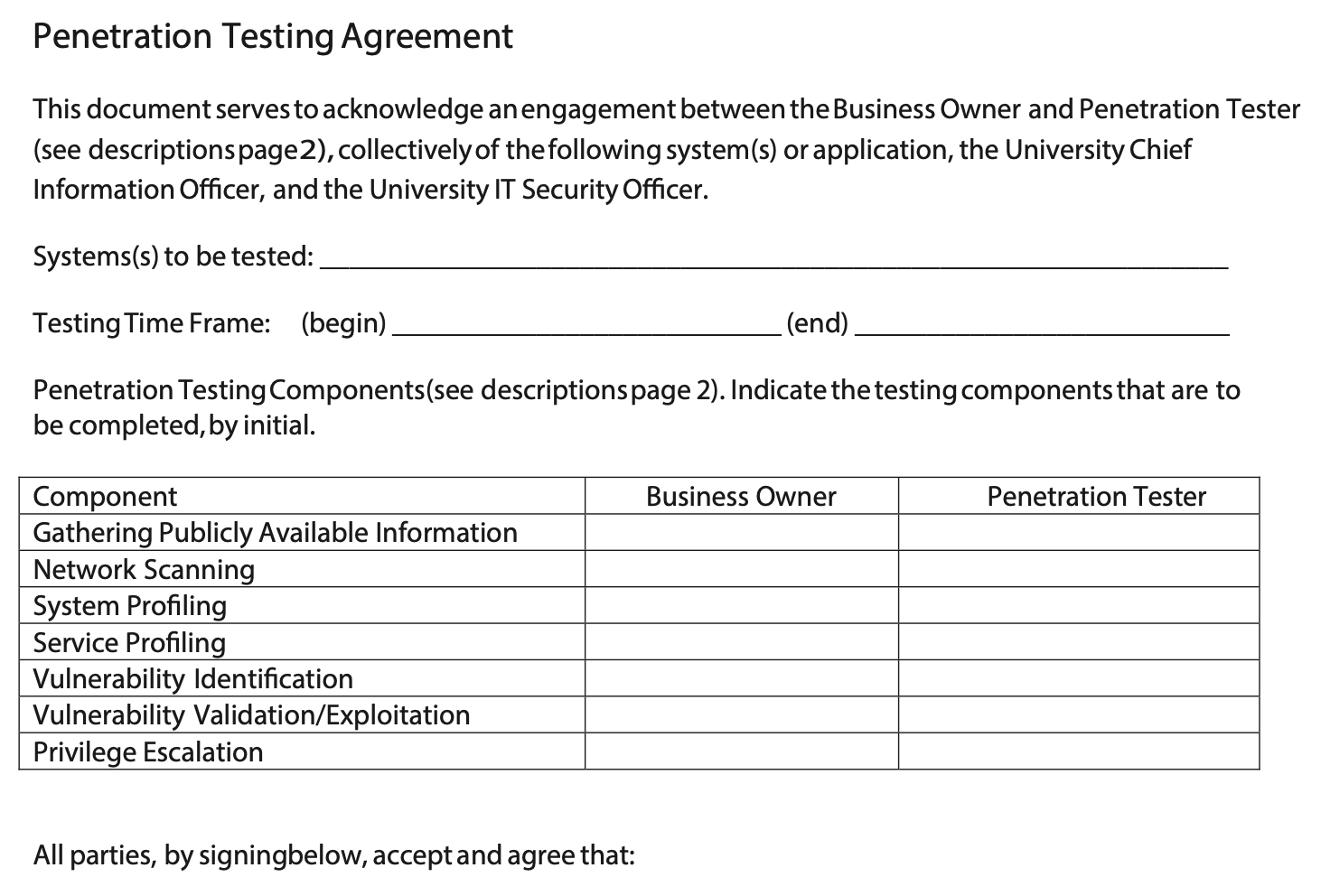 CorrectIncorrect
CorrectIncorrect -
Question 4 of 10
4. Question
You have been hired by a company to implement a solution to make sure that non-employees have access privileges to the network that are separate from those of employees. Which of the following solutions should you implement?
CorrectIncorrect -
Question 5 of 10
5. Question
You have been hired to perform a pen test on the wireless network of the Acme Corporation. What do you need to know before starting the assessment process?
CorrectIncorrect -
Question 6 of 10
6. Question
What type of document is used to describe the work requirements for a specific project along with its performance and design expectations?
CorrectIncorrect -
Question 7 of 10
7. Question
A penetration tester performing a pentest on the network of the Acme corporation. Once he tried to connect to the network the IPS/IDS system blocked his workstation, as it appeared a suspicious device. Which of the following features should the company use to allow the pentester to continue his work.
CorrectIncorrect -
Question 8 of 10
8. Question
You are performing a penetration test for a hospital that has requested the pentest because it controls the handling of health records from patients. Which of the following type of assessment is being performed?
CorrectIncorrect -
Question 9 of 10
9. Question
A hacker wants to attack a network with the aim of maintaining ongoing access to the targeted network rather than to get in and out as quickly as possible with the ultimate goal of stealing information over a long period of time. What type of attacking technique will the hacker use in this case?
CorrectIncorrect -
Question 10 of 10
10. Question
The document that lists out the specifics of your penetration testing project to ensure that both the client and the engineers working on a project know exactly what is being tested when it’s being tested, and how it’s being tested is known as:
CorrectIncorrect