Time limit: 0
Quiz Summary
0 of 25 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Quiz complete. Results are being recorded.
Results
0 of 25 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Unfortunately, you didn’t pass the quiz, but hey, you have unlimited access.😎
Practice makes you perfect! 👊 -
Congratulations! 🥳
You have passed the quiz successfully! You are one step closer to pass the real exam!
We hope to see you again on another certification path.✌️
Good luck with the exam! Stay strong.👊
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 25
1. Question
You have recently been hired as an IT security specialist by a small company to improve the security of their wireless network. You have been tasked to harden the wireless network infrastructure to the highest possible level. Which of the following protocol encryption methods should you implement for the BEST security? (Choose all that apply.)
CorrectIncorrect -
Question 2 of 25
2. Question
Your friend recently heard the flaw in Windows 10 could cause a PC to bluescreen–even when locked–by simply inserting a malicious USB drive. He comes to you for advice on how to eliminate this flaw. Which of the following actions should your friend perform to prevent this type of attack from occurring?
CorrectIncorrect -
Question 3 of 25
3. Question
A hacker works through all possible combinations hoping to guess login credentials correctly. Which type of attack would this BEST be categorized as?
CorrectIncorrect -
Question 4 of 25
4. Question
The workstations in the IT department have been compromised by a hacker and used for DDoS attacks. Which of the following word BEST describes the compromised workstations in the IT department?
CorrectIncorrect -
Question 5 of 25
5. Question
You have just received an email from your bank stating that you need to change the e-banking password by pressing a button that says “Reset your password here”. The password of your e-banking has already been changed a week ago and this email seems suspicious. Which of the following best describes this type of attack?
CorrectIncorrect -
Question 6 of 25
6. Question
After downloading a file from the web, you start noticing your workstation behaving weirdly. Two days later you receive an email from an unknown source stating that the workstation is hacked and now they can use the device to mine for cryptocurrency. Which type of malware MOST likely infected your workstation?
CorrectIncorrect -
Question 7 of 25
7. Question
Your friend Steve worries that if his smartphone is stolen or lost, the sensitive data the phone contains might be exposed to the wrong person. He wants to find a way to secure the device in case of loss. Which of the following is the BEST method of securing the phone?
CorrectIncorrect -
Question 8 of 25
8. Question
Which of the following describes the security method that permits a user to use one set of login credentials — for example, a name and password — to access multiple applications?
CorrectIncorrect -
Question 9 of 25
9. Question
You have been tasked to improve the security of the company’s network infrastructure. The task is to provide a way to authenticate the employees for accessing the corporate wireless network and other network resources before gaining access. Which of the following authentication methods should you implement to complete the task?
CorrectIncorrect -
Question 10 of 25
10. Question
You have been hired to provide a solution to a well-known hotel chain. The hotel manager wants to keep the wireless network open and free for all guests but also wants to prevent people in the neighborhood from accessing it. What will you do to achieve that?
CorrectIncorrect -
Question 11 of 25
11. Question
You have three (3) old laptops sitting at your home and you are thinking to give them away to your friends. You want to make sure that all data should be deleted before sharing the laptops. Which of the following data destruction and disposal methods should you execute to allow the data on the drives to be fully destroyed?
CorrectIncorrect -
Question 12 of 25
12. Question
Given the following wireless security protocols and encryption methods, which of the following is the LEAST secure and you have to avoid using it?
CorrectIncorrect -
Question 13 of 25
13. Question
Which of the following physical security measures you should implement in order to protect yourself from shoulder surfing attacks?
CorrectIncorrect -
Question 14 of 25
14. Question
You are setting up a new wireless network in your company’s data center. The wireless network should allow only four (4) devices to be connected and block the rest. The four (4) devices are three (3) wireless cameras and one (1) mobile phone. Based on the requirements provided, which of the following configuration settings should you use to meet the requirement?
CorrectIncorrect -
Question 15 of 25
15. Question
A corporate workstation was recently infected with malware. The malware began to infect other workstations on the same network using the credentials it stole from the first workstation. As a result, the whole network was affected and all devices within the network became unavailable. You have been tasked to find a way to prevent this incident from occurring again. Which of the following actions should you take to prevent this from reoccurring?
CorrectIncorrect -
Question 16 of 25
16. Question
You just got notified that the web server of your company is experiencing a DDoS attack. Twenty (20) internal devices are infected with malware and the cybercriminal uses them to carry out the attack against the web server. Which of the following BEST describes the infected computers?
CorrectIncorrect -
Question 17 of 25
17. Question
A new policy dictates that the employee’s responsibilities will be controlled based on the job functions and tasks within the company. That means, a user account created for pulling records from a database doesn’t need admin rights, while a developer whose main function is updating lines of code doesn’t need access to financial records. Which of the following security concepts is BEST described by this new policy?
CorrectIncorrect -
Question 18 of 25
18. Question
Which of the following would provide the BEST security solution for both computers and smartphones?
CorrectIncorrect -
Question 19 of 25
19. Question
When you are trying to log in to your Facebook account, you are asked to enter your username and password. Which type of authentication method is Facebook using in this case?
CorrectIncorrect -
Question 20 of 25
20. Question
Which of the following security measures should you take to increase the security of physical spaces such as server rooms? (Choose all that apply.)
CorrectIncorrect -
Question 21 of 25
21. Question
ExamsDigest has just set up a new lab consisting of eight (8) laptops four (4) Cisco routers and twelve (12) Cisco switches to allow students to gain hands-on experience using live equipment. The Cisco products are locked in a rack but the laptops are exposed to the public as the lab is open 24/7. Which of the following physical security measures should be used to ensure the laptops are not stolen or moved out of the lab environment?
CorrectIncorrect -
Question 22 of 25
22. Question
You receive a call from the senior network engineer of your company saying that the web server is infected with malware. All the .html, .css, .js and .php files on the server appear to be encrypted and locked. In addition, he received the following warning message asking for bitcoin — as shown in the image below — in order to get the files back:
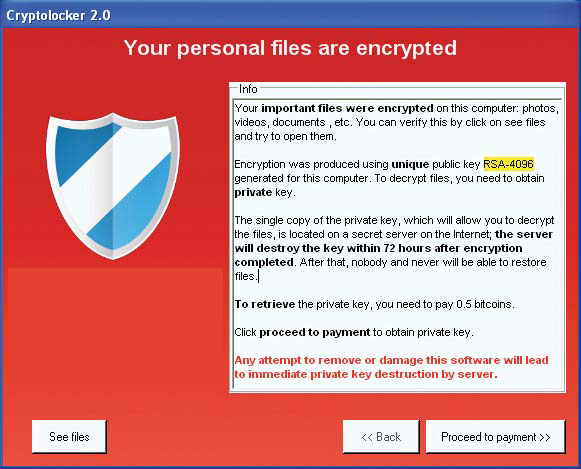
Which type of malware MOST likely infected the web server?
CorrectIncorrect -
Question 23 of 25
23. Question
You are configuring a SOHO (Small Office/Home Office network) router in your home. You want to harden the wi-fi network as much as possible, by using the latest encryption technologies and prevent your neighbors to connect to it. Which of the following actions should you perform to increase the security of your home’s wireless network? (Choose all that apply.)
CorrectIncorrect -
Question 24 of 25
24. Question
Your neighbor’s wireless network was compromised by a hacker who used an attack named brute force attack. The hacker got administrative rights and changed all the default settings inside the wireless access point. Which of the following configurations was most likely used to allow the attack to occur?
CorrectIncorrect -
Question 25 of 25
25. Question
You have been tasked to give the correct type of user accounts to all interns/trainees to have the bare minimum privileges to perform only specific tasks using the company’s workstations. Which of the following types of user accounts should interns/trainees be given to perform their jobs?
CorrectIncorrect